Main > Statistics
|
We tested 450,000 potentially vulnerable web resources in 17 countries. Critical SQL vulnerabilities were found in more than 165 thousand domains.
With these SQL vulnerabilities, an attacker can access any information of a web resource database.
|
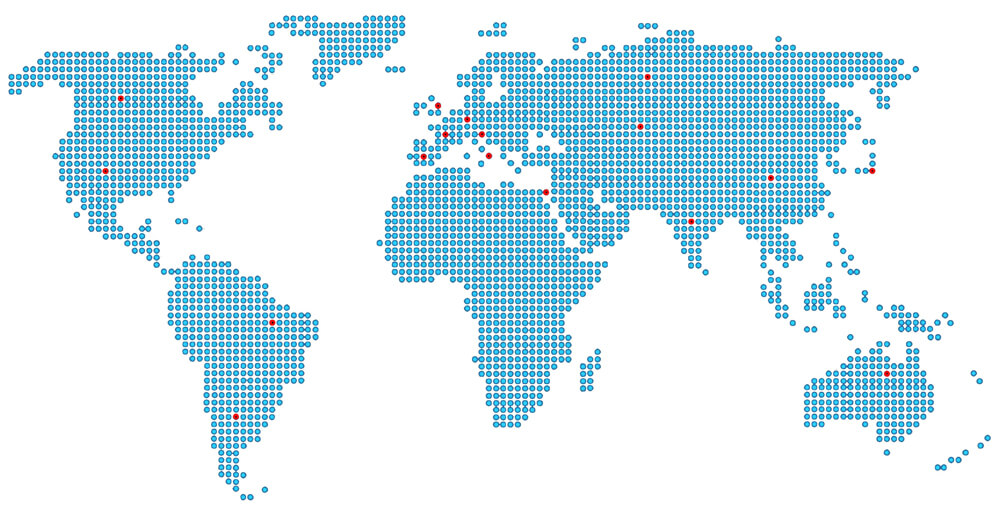
Vulnerable Resources Map (Scanning SFO and SSO )
|
|

|
Statistics
|
37% of web resources, which have been scanned in the research, have at least one SQL injection, and the this web resource database can be completely compromised by automatic means. Such conclusions are contained in the 2016 SQL Vulnerability Study by ISAWT. A fragment of the paper is given below. The study scanned 450,000 web-resources in 17 national domain zones. The scanning was carried out by black-box testing according to the SFO and SSO standards adopted by ISAWT without utilization of the revealed SQL vulnerabilities. The study involved the Security-Scan multi-threaded modular scanner and an optional ISAnalyzer module for processing the scan results. In the study, the world's largest national domain zones are presented, as well as rather small ones. The most popular open domain zones .com, .net, .org, .biz are not presented in the study, because determining the nationality of the resources registered in them is impossible. |
The ISAWT adopted several scanning standards: SFO (Scanning of First Order) is performed for statistical data collection by intact coating or by defined geographical areas. WITHOUT penetration into the structure of the web-resource and WITHOUT any change in its work. The result is a list of potentially vulnerable web resources. SSO (Scanning of Second Order) is performed for studying the statistics of specific vulnerabilities within the database of potentially vulnerable domains identified during the SFO. WITHOUT any change in the operation of the web-resource. The result is a list of web resources with critical vulnerabilities. FS (Full Scanning) is performed with a specific web resource across the entire set of vulnerabilities. Web-resource entry WITHOUT its work violation. The result is a list of vulnerabilities in a particular web resource for further analysis and development of a Security Policy. |
|
The most carefree programmers live in India India, Great Britain, China, USA and Australia are the SQL vulnerable web-resources leaders among checked domains. The largest and richest countries in the world, where the Internet is sequence more developed than in Russia, are outsiders in terms of the SQL injections security. Apparently, the most relaxed programmers live in India; and the most cautious among 17 tested countries live in Brazil, Germany, France, Russia and Kazakhstan. The development of the Internet in Kazakhstan is much slower than in all 17 countries chosen for scanning. How could Kazakhstan become the leader in the reliability of protection against SQL injection? The Internet traffic rates are many times lower than those of neighboring Russia or Israel, which is closest to Kazakhstan from the 17 states represented by the number of domains. But, nevertheless, the percentage of the SQL vulnerable resources from the number of tested is much lower (21% vs. 39%) than in Israel. |
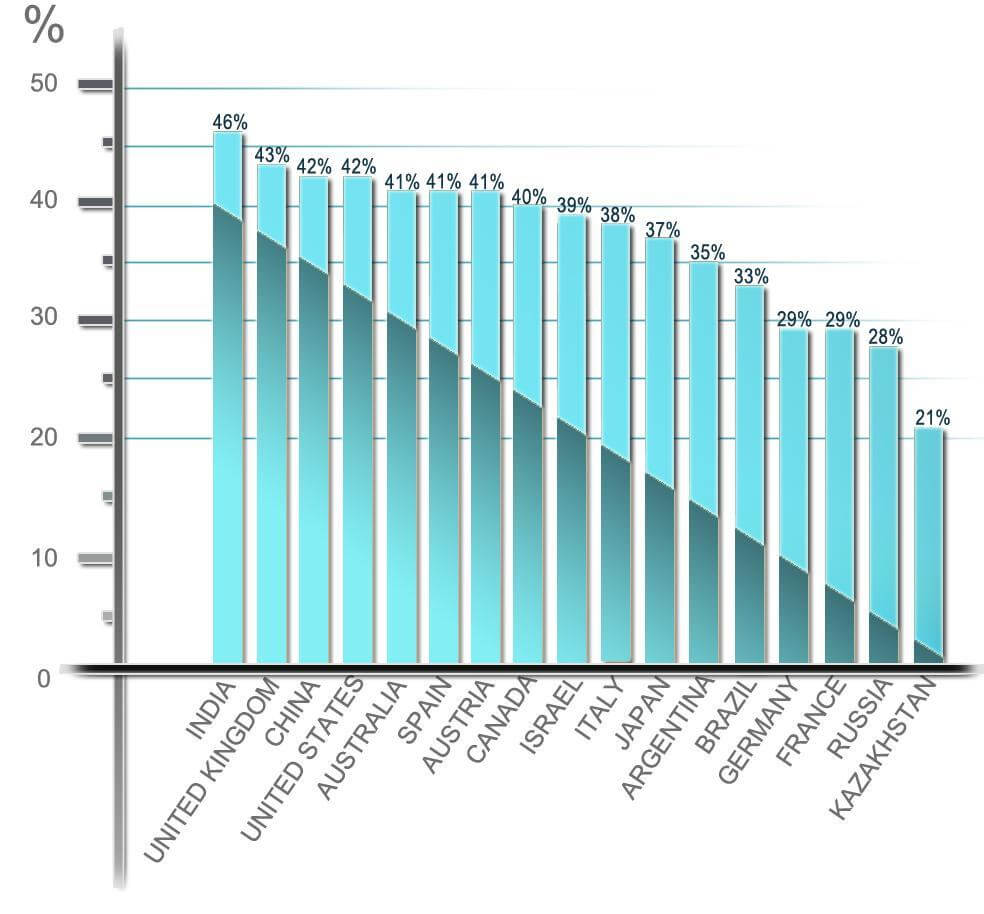 Fig. 1 SQL vulnerable resources amongst scanned |
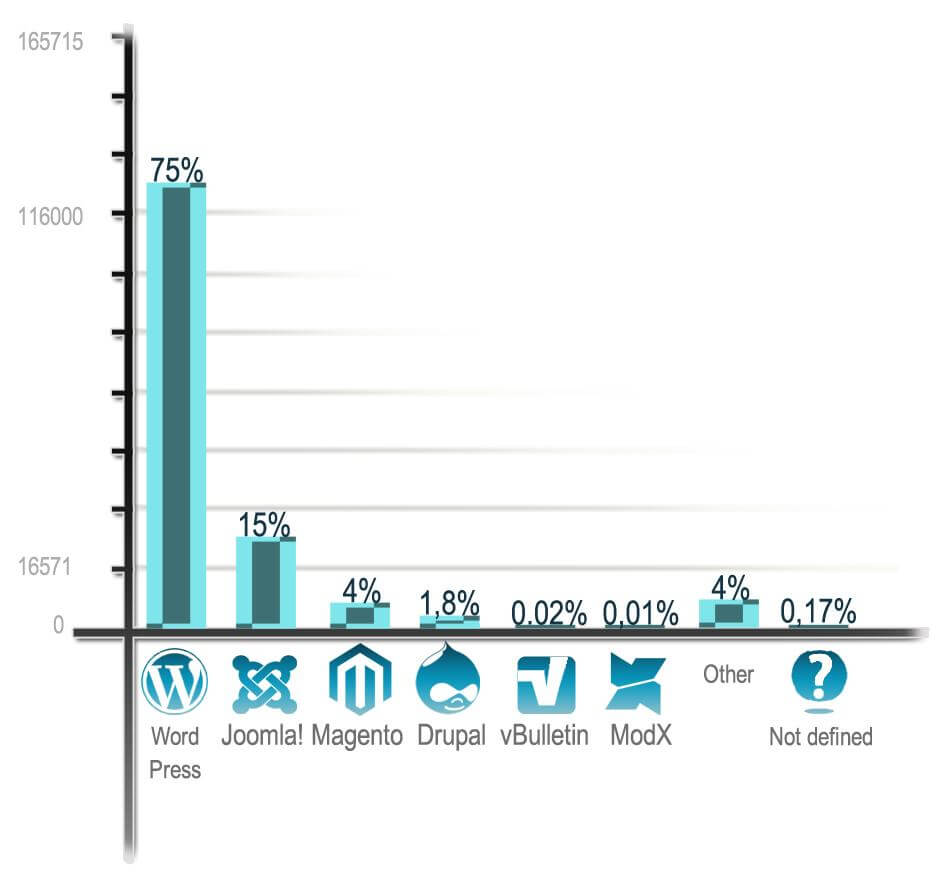 Fig. 2 CMS platforms of SQL-vulnerable web resources |
The share of Russian Internet resources in the .KZ domain zone significantly exceeds the share of national resources. Developers of such resources are often Russian companies or outsourcers from Russia and Ukraine. This explains the high level of security of web-resources in the .KZ zone at rather low development rates of the national Internet. Unlike Kazakhstan, Germany is an unattainable giant in terms of the number of registered domains and Internet traffic in its national zone among the countries selected for scanning, but it also has quite high indicators of security from the SQL injections. Thus, the scan results clearly demonstrate the independence of the security indicators of web-resources from the Internet development level, as well the Internet traffic rates in the country. |
|
First in everything WordPress The most popular CMS platforms WordPress, Joomla! and Magento turned out to be the fattest in SQL vulnerability, but this does not mean that they are less secure; they are just more common than others. WordPress is an undisputed leader among the used CMS platforms. 75% of all SQL-vulnerable web resources found in the study are coded on this platform. WordPress is practically a monopolist. Therefore, the vulnerability indicators are the highest, with multiple breakaway from the closest competitors. Updates Surely most Internet and PC users are bored with constantly updating various software, especially if it is already set up and operates properly. In the case of the CMS platforms, laziness can lead you down. The share of web-resources with critical SQL vulnerabilities that use legacy software is impressive with its scale. The lowest index of the most common CMS platforms is more than 50%! |
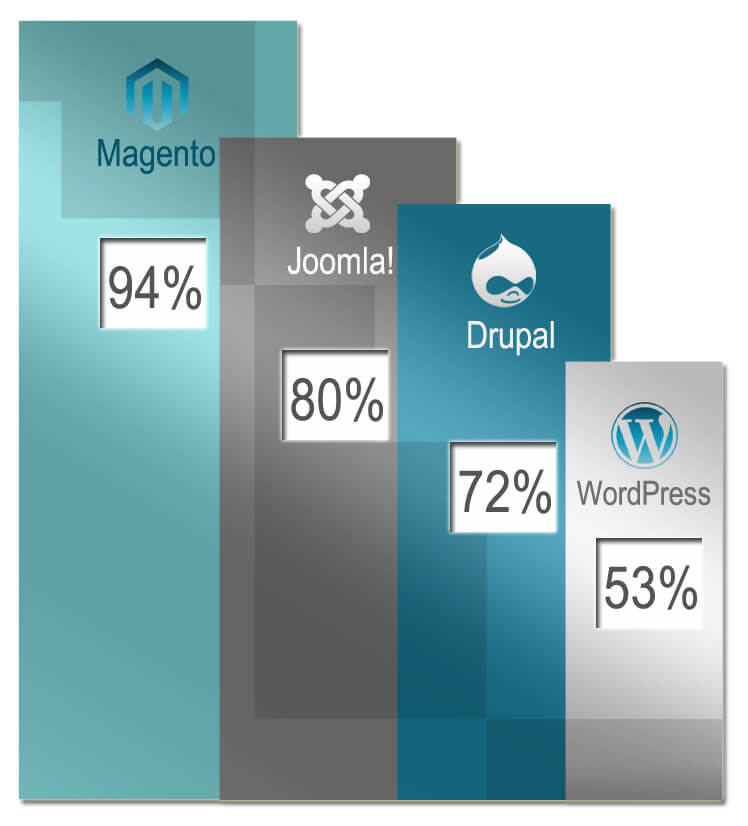 Fig. 3 Percentage of legacy CMS software on SQL vulnerable resources |
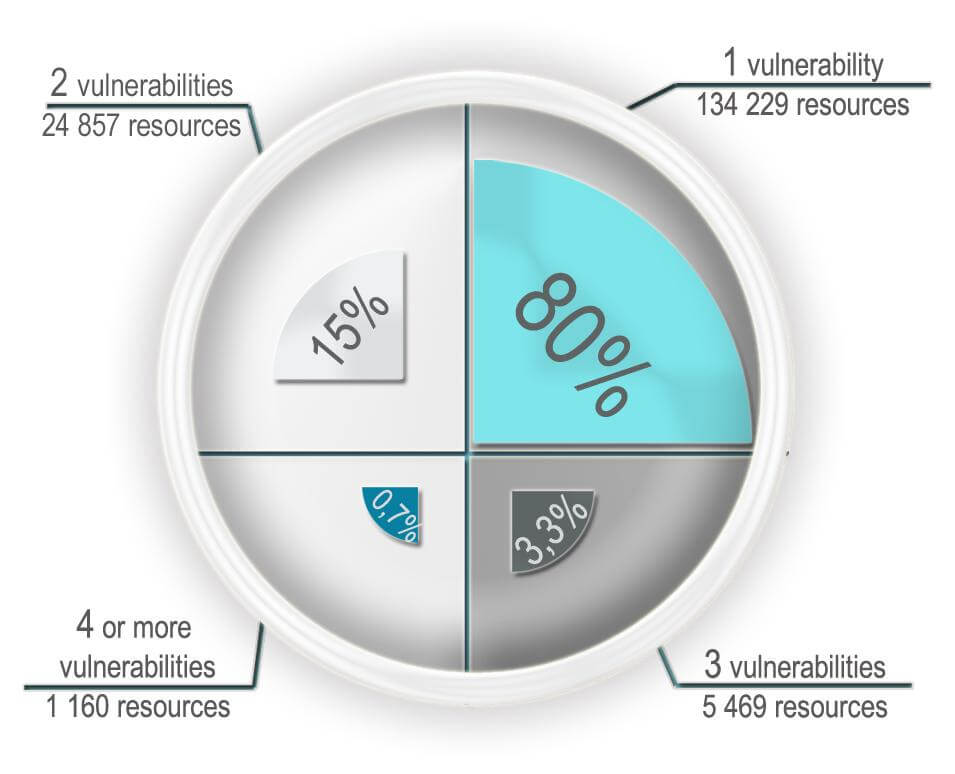 Fig. 4 Number of vulnerabilities for 1 web resource |
94% of the detected SQL vulnerable resources on the Magento platform run on legacy software, vs. 53% on the most common WordPress platform. The Magento developers should be more active in promoting the updates among their adherents. Admins are humans too, but the lack of effective administration of systems just leads to such remarkable results. Qualitative Analysis The nature of the detected SQL vulnerabilities allows us to assert that each of 165,000 web-resources containing these vulnerabilities can be successfully attacked automatically. 19% of 165,000 resources had 2 or more SQL vulnerabilities. |
Errors in programming and administration are in the first place in terms of critical impact on the overall security of web resources. To prevent any attempts of external attacks, you may need not only to create resources, but also to know how they can be destroyed. Thinking like a criminal and being one step ahead of him on the issue of defense is the only reliable way to secure.
Summary
Thus, the main reasons that affect the susceptibility of web resources to SQL injection are errors in system development, legacy software, vulnerable extensions, and insufficiently effective system administration. Therefore, in order to protect your databases from unauthorized access, you need a set of measures from instructing staff and eliminating computer illiteracy to developing a security strategy and installing specialized software to intercept external attacks and ensure information security.
Summary
Thus, the main reasons that affect the susceptibility of web resources to SQL injection are errors in system development, legacy software, vulnerable extensions, and insufficiently effective system administration. Therefore, in order to protect your databases from unauthorized access, you need a set of measures from instructing staff and eliminating computer illiteracy to developing a security strategy and installing specialized software to intercept external attacks and ensure information security.
|
37% of web resources, which have been scanned in the research, have at least one SQL injection, and the this web resource database can be completely compromised by automatic means. Such conclusions are contained in the 2016 SQL Vulnerability Study by ISAWT. A fragment of the paper is given below. The study scanned 450,000 web-resources in 17 national domain zones. The scanning was carried out by black-box testing according to the SFO and SSO standards adopted by ISAWT without utilization of the revealed SQL vulnerabilities. The study involved the Security-Scan multi-threaded modular scanner and an optional ISAnalyzer module for processing the scan results. In the study, the world's largest national domain zones are presented, as well as rather small ones. The most popular open domain zones .com, .net, .org, .biz are not presented in the study, because determining the nationality of the resources registered in them is impossible. |
|
The ISAWT adopted several scanning standards: SFO (Scanning of First Order) is performed for statistical data collection by intact coating or by defined geographical areas. WITHOUT penetration into the structure of the web resource and WITHOUT any change in its work. The result is a list of potentially vulnerable web resources. SSO (Scanning of Second Order) is performed for studying the statistics of specific vulnerabilities within the database of potentially vulnerable domains identified during the SFO. WITHOUT any change in the operation of the web resource. The result is a list of web resources with critical vulnerabilities. FS (Full Scanning) is performed with a specific web resource across the entire set of vulnerabilities. Web-resource entry WITHOUT its work violation. The result is a list of vulnerabilities in a particular web resource for further analysis and development of a Security Policy. |
|
The most carefree programmers live in India India, Great Britain, China, USA and Australia are the SQL vulnerable web-resources leaders among checked domains. The largest and richest countries in the world, where the Internet is sequence more developed than in Russia, are outsiders in terms of the SQL injections security. Apparently, the most relaxed programmers live in India; and the most cautious among 17 tested countries live in Brazil, Germany, France, Russia and Kazakhstan. The development of the Internet in Kazakhstan is much slower than in all 17 countries chosen for scanning. How could Kazakhstan become the leader in the reliability of protection against SQL injection? The Internet traffic rates are many times lower than those of neighboring Russia or Israel, which is closest to Kazakhstan from the 17 states represented by the number of domains. But, nevertheless, the percentage of the SQL vulnerable resources from the number of tested is much lower (21% vs. 39%) than in Israel. The share of Russian Internet resources in the .KZ domain zone significantly exceeds the share of national resources. Developers of such resources are often Russian companies or outsourcers from Russia and Ukraine. This explains the high level of security of web-resources in the .KZ zone at rather low development rates of the national Internet. Unlike Kazakhstan, Germany is an unattainable giant in terms of the number of registered domains and Internet traffic in its national zone among the countries selected for scanning, but it also has quite high indicators of security from the SQL injections. Thus, the scan results clearly demonstrate the independence of the security indicators of web-resources from the Internet development level, as well the Internet traffic rates in the country. |
 Fig. 1 SQL vulnerable resources amongst scanned |
|
First in everything WordPress The most popular CMS platforms WordPress, Joomla! and Magento turned out to be the fattest in SQL vulnerability, but this does not mean that they are less secure; they are just more common than others. WordPress is an undisputed leader among the used CMS platforms. 75% of all SQL-vulnerable web resources found in the study are coded on this platform. WordPress is practically a monopolist. Therefore, the vulnerability indicators are the highest, with multiple breakaway from the closest competitors. |
 Fig. 2 CMS platforms of SQL-vulnerable web resources |
|
Updates Surely most Internet and PC users are bored with constantly updating various software, especially if it is already set up and operates properly. In the case of the CMS platforms, laziness can lead you down. The share of web-resources with critical SQL vulnerabilities that use legacy software is impressive with its scale. The lowest index of the most common CMS platforms is more than 50%! 94% of the detected SQL vulnerable resources on the Magento platform run on legacy software, vs. 53% on the most common WordPress platform. The Magento developers should be more active in promoting the updates among their adherents. Admins are humans too, but the lack of effective administration of systems just leads to such remarkable results. |
 Fig. 3 Percentage of legacy CMS software on SQL vulnerable resources |
|
Qualitative Analysis The nature of the detected SQL vulnerabilities allows us to assert that each of 165,000 web-resources containing these vulnerabilities can be successfully attacked automatically. 19% of 165,000 resources had 2 or more SQL vulnerabilities. Errors in programming and administration are in the first place in terms of critical impact on the overall security of web resources. To prevent any attempts of external attacks, you may need not only to create resources, but also to know how they can be destroyed. Thinking like a criminal and being one step ahead of him on the issue of defense is the only reliable way to secure. |
 Fig. 4 Number of vulnerabilities for 1 web resource |
|
Summary Thus, the main reasons that affect the susceptibility of web resources to SQL injection are errors in system development, legacy software, vulnerable extensions, and insufficiently effective system administration. Therefore, in order to protect your databases from unauthorized access, you need a set of measures from instructing staff and eliminating computer illiteracy to developing a security strategy and installing specialized software to intercept external attacks and ensure information security. |